
Table of Contents
Introduction to Dark Web
The dark web is one of the most mysterious and misunderstood parts of the internet. Many have heard of it, but few truly understand what it is or how it works. At the heart of accessing the dark web are specialized tools called dark web browsers. These browsers allow users to navigate through the hidden layers of the internet, places that aren’t indexed by traditional search engines. But what exactly is a dark web browser, and why do people use it? Let’s dive in and find out.
The Layers of the Web: Surface, Deep, and Dark
Before we get into the specifics of dark web browsers, it’s important to understand the structure of the internet. There are three key layers:
- Surface Web: This is the part of the web you use every day. It’s where websites like Google, Facebook, and Wikipedia reside. This content is easily accessible via regular browsers like Chrome or Firefox.
- Deep Web: The deep web includes content that is not indexed by search engines. Think of things like password-protected databases, personal email accounts, and subscription-based services.
- Dark Web: The dark web is a smaller section of the deep web, intentionally hidden and often associated with anonymity and privacy. You can only access it using specific browsers.
What is a Dark Web Browser?
A dark web browser is a specialized tool that allows users to access websites on the dark web. Unlike regular websites that end in domains like “.com” or “.org,” dark web websites typically end in “.onion.” These “.onion” sites cannot be accessed with a standard browser. Instead, you need a dark web browser like TOR (The Onion Router), which is the most popular option.
How Dark Web Browsers Work
Dark web browsers work differently from traditional browsers. Instead of directly connecting to a website, they use complex encryption techniques and multiple layers of routing to mask a user’s identity and location. This ensures that users remain anonymous, and their activities are harder to trace.
TOR Browser: The Most Popular Dark Web Browser
The TOR browser is by far the most commonly used dark web browser. Originally developed by the U.S. Navy for secure communication, TOR now serves as a tool for privacy enthusiasts, journalists, and even whistleblowers. It encrypts your data and sends it through multiple servers, or “nodes,” to keep your identity private.
Alternatives to TOR Browser
Although TOR is the most well-known, it’s not the only option for accessing the dark web. Alternatives include:
- I2P (Invisible Internet Project): Known for its strong focus on privacy, I2P is a decentralized network that ensures secure communication between users.
- Freenet: Another dark web tool, Freenet is primarily focused on free speech and bypassing censorship. It allows users to share files and chat anonymously.
Key Features of Dark Web Browsers
Dark web browsers offer more than just access to hidden websites. They are packed with features designed to enhance user privacy, ensure anonymity and provide a safe browsing experience. Let’s look at some of the key features that set these browsers apart:
- Layered routing (onion routing): As mentioned above, dark web browsers like TOR use a unique method called onion routing. This involves encrypting your data multiple times and sending it through different servers (or nodes). Each node peels back a layer of encryption before passing the data to the next node. The process is similar to peeling back the layers of an onion, hence the name. This multi-layered approach ensures that no single node knows both your origin and destination, making your online activity much harder to trace.
- Advanced encryption and privacy: One of the most important features of dark web browsers is their ability to encrypt user data. When you use a dark web browser, your online activity is wrapped in multiple layers of encryption, making it difficult for anyone – including Internet Service Providers (ISPs) or government agencies – to track your movements. This encryption applies to both your browsing data and the location of the websites you visit.
- IP address masquerading: Dark Web browsers like TOR automatically mask your IP address by routing your traffic through a network of volunteer-operated servers. This process ensures that your actual location and identity remain hidden, adding an extra layer of security. Unlike regular browsers, which expose your IP address to every site you visit, Dark Web browsers mask your presence, making it much harder for anyone to track your whereabouts.
- Access to .onion websites: Dark Web browsers allow access to .onion websites, which are not indexed by traditional search engines and are hidden from standard browsers. These sites operate in a separate namespace from typical domains such as “.com” or “.org”. To visit these sites, you mustto use a Dark Web browser that can interpret the unique structure of these hidden URLs. This feature is essential for those seeking content or services not available on the surface web.
- Resistance to tracking and surveillance: Another important feature of dark web browsers is their resistance to the tracking mechanisms commonly used on the surface web. Many websites on the surface web use cookies, third-party scripts and fingerprinting techniques to track users. Dark web browsers are designed to block these tracking methods, preventing websites from collecting data about your browsing habits or personal information. Some browsers, such as TOR, go even further by deleting cookies and browsing history after each session to maintain anonymity.
- Decentralised network: The Dark Web relies on a decentralised network of volunteer-run servers to function. This setup means that there is no central authority or server controlling the entire network, making it more resilient to shutdowns or attacks by governments or corporations. Users can also contribute by running their own TOR nodes, making the network even more resilient.
- No single point of failure: Unlike traditional browsing, where traffic is routed through centralised servers controlled by specific organisations, the decentralised nature of the dark web ensures that no single entity can control or monitor all activity. This not only makes it harder for governments or hackers to shut down or monitor the network, but also spreads the risk across a wider range of servers.
Onion Routing Explained
Onion routing is the backbone of the TOR network. It’s called “onion” because, like peeling an onion, data is encrypted in multiple layers. Each layer is decrypted at a different node (server), meaning no one node can see both your IP address and your destination at the same time.
The Appeal of Dark Web Browsers
So why do people use dark web browsers? There are several legitimate reasons, though it’s important to note that the dark web is also home to illegal activities.
Reasons People Use Dark Web Browsers
- Privacy: For those who value their privacy and want to avoid tracking by advertisers, governments, or hackers, dark web browsers offer a sense of security.
- Access to Censored Information: In some countries, access to certain websites is restricted or censored. Dark web browsers allow users to bypass these blocks.
- Whistleblowing and Journalism: Many journalists and whistleblowers use the dark web to communicate sensitive information without revealing their identity.
The Risks and Dangers of Using a Dark Web Browser
While dark web browsers provide anonymity, they also come with significant risks.
Illegal Activities and Cybercrime
Unfortunately, the dark web is a hub for illegal activities, including the sale of drugs, weapons, and stolen data. Just because you can browse anonymously doesn’t mean you’re immune to law enforcement. Engaging in illegal activities can still get you into trouble.
Case of Silk Road Dark Market
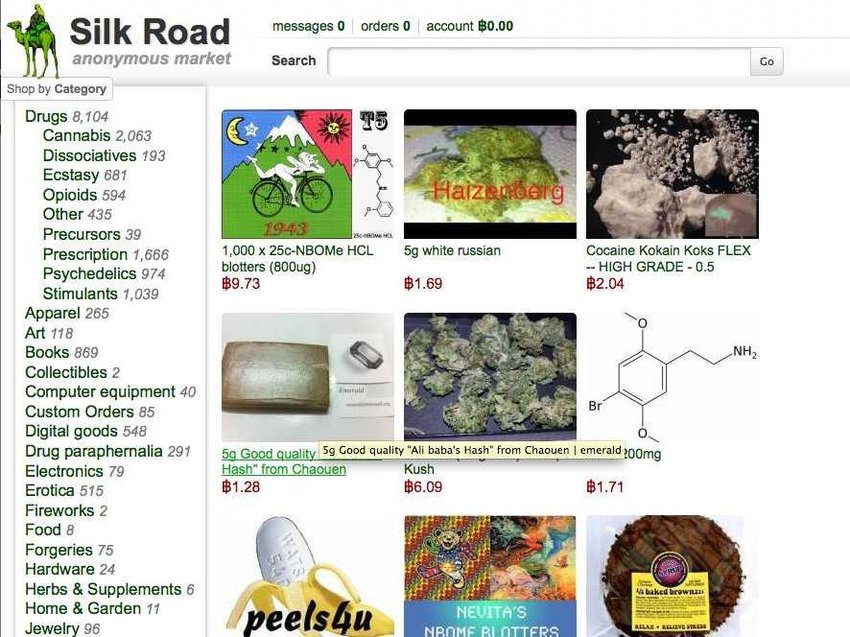
The Silk Road was one of the most notorious marketplaces on the dark web, launched in 2011. It operated on the TOR network and allowed users to buy and sell illegal goods, primarily drugs, using Bitcoin for anonymous transactions. Founded by Ross Ulbricht under the pseudonym “Dread Pirate Roberts,” Silk Road quickly drew the attention of law enforcement for facilitating illegal activities. In 2013, the FBI shut down the marketplace, and Ulbricht was arrested and sentenced to life in prison. The takedown of the Silk Road highlighted both the risks and the anonymity offered by dark web browsers.
Security Threats and Malware
The dark web is also riddled with malware and hackers waiting to exploit unsuspecting users. Even if you’re careful, downloading files or clicking on suspicious links can expose your device to harmful software.
How to Safely Use a Dark Web Browser
If you’re going to use a dark web browser, it’s crucial to take precautions.
Best Practices for Dark Web Browsing
- Use a VPN: Always use a VPN in conjunction with a dark web browser to add an extra layer of security. My favourite VPN provider is NordVPN (no affiliate)
- Avoid Downloading Files: Many files on the dark web contain malware. Stick to browsing, and don’t download anything unless you know it’s safe.
- Stay on Trusted Sites: Only visit reputable websites and avoid sketchy links or services that seem too good to be true.
- User Safe Search Engines: When navigating the dark web, it’s important to use search engines specifically designed for it, as regular search engines like Google won’t index .onion sites. Safe search engines such as DuckDuckGo or Ahmia prioritize privacy and don’t track your searches. Don’t forget also to read our article about hacker’s search engines to see what search engines are the best for hackers. Using the right search engine reduces the risk of landing on malicious sites or revealing personal information while browsing.
Should You Use a Dark Web Browser?
While Dark Web browsers have legitimate uses, they’re not for everyone. If you’re just curious, it’s important to weigh the risks and potential rewards before diving in.
Legal and Ethical Considerations
Using a Dark Web browser is not illegal, but engaging in criminal activity on the Dark Web is. Always make sure you stay on the right side of the law and use these tools ethically and responsibly.
Conclusion: Navigating the Dark Web with Caution
In conclusion, dark web browsers like TOR offer a powerful way to protect your privacy and access information that might otherwise be out of reach. However, they also come with significant risks, from malware to legal trouble. If you decide to explore the Dark Web, do so with caution, and always keep your safety and security in mind.
FAQ
Is using a dark web browser illegal?
No, using a dark web browser like TOR is not illegal. However, engaging in illegal activities on the dark web is.
Can I access the dark web with a regular browser?
No, regular browsers like Chrome or Firefox cannot access dark web sites. You need a browser like TOR.
Is TOR completely anonymous?
TOR offers a high level of anonymity, but it’s not foolproof. Using a VPN alongside TOR is recommended for added security.
What can I find on the dark web?
The dark web hosts a range of content, from whistleblower platforms to illegal marketplaces. Be cautious when exploring.
Can I get viruses from the dark web?
Yes, malware is rampant on the dark web. Avoid downloading files or clicking suspicious links.

