The internet provided a way to connect people around the world. However, as everything has its pros and cons, the same applies to the internet. An average internet user may not be aware of the risks or threats that the use of internet has. Especially if you operate a business or company, then it is mandatory to know about the current cyber threats.
In this article, we are going to explore the Top 10 cyber threats from 2020 until today (2022) as presented by ENISA.
The list with the Top 10 Cyber Threats is the following :
- Malware
- Web-based Attacks
- Phishing
- Web Application Attacks
- SPAM
- Distributed Denial of Service (DDoS)
- Identity Theft
- Data Breach
- Insider Threat
- Botnets
Threats Explanation
Many of the above threats have been well known for many years while others were discovered recently. But let’s try to explain them with simple words:
1. Malware:
The term “malware” refers to a broad category of harmful software or programs that can be deployed for a variety of purposes. This could include stealing your personal data, gaining access to your accounts, or even shutting down your computer. So it can damage you or your computer.
Some well-known malware categories are virus, worms, spyware, adware, trojans, and ransomware (even though it is listed as a different category).
The main point to keep in mind is that irrespective of the malware type, hackers usually attempt to steal anything valuable (personal data, card numbers, telephone number etc.) from your mobile or your PC without showing any sign. So, it is important to understand the risks and develops proper cyber skills to avoid getting breached.
2. Web-based attacks:
The second threat is related to attacks that use web systems and services to trick victims. Attackers use different web-based methods for achieving this; sending malicious URLs to user for directing it to malicious websites, downloading malicious content from a website, or injecting malicious code into trustworthy websites in order to steal information from users. Moreover, the most common way of delivering a malicious link or URL to the user is the email.
The ultimate goal of those attacks is to steal information for financial gain, information theft, or even ransomware extortion.
Sometimes Web-based attacks can be combined with Phishing attacks ( see below) to achieve user’s information theft.
3. Phishing:
A well-known email-related threat is Phishing. Attackers seek to gather sensitive information, including passwords and credit card data, using emails. The way that hackers convince the victim to give them information is called social engineering. Actually, hackers try to psychologically manipulate users (by presenting valid statements) to perform actions or disclose confidential information.
Stages of phishing attacks
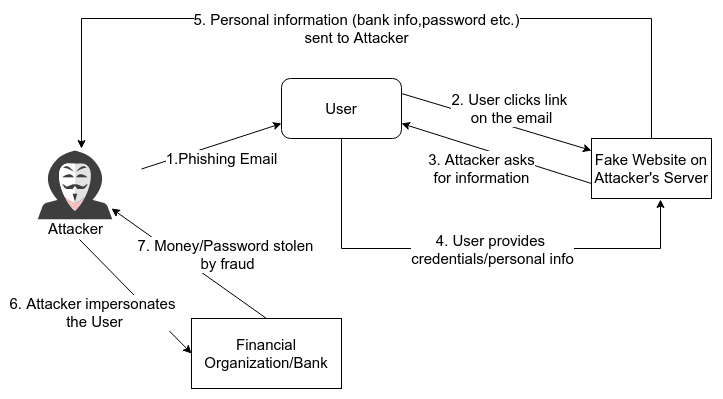
In the above diagram, we demonstrate the stages that attackers usually follow to achieve Phishing attacks. Initially, an email with fake information (“Phishing Email”) is sent to the Victim/User. The user is tricked using social engineering to click the link that is presented in the email. Once user clicks the link, a fake website that is hosted by attacker is loaded. The website contains usually a login form or some fields to fulfill your personal information. At step 5, the victim submitted its personal information and those are transferred to the attacker. Now, the attacker has all the required information to impersonate the victim to the Bank or any other organization in order to steal money. In addition, user’s details can be used to hack any type of online account or even use user’s active subscriptions without getting notice e.g. Netflix account.
Phishing Emails
Let’s see an example of how you can get directed to a malicious website. Look at the image below. You see that an email is pretending to be from “Microsoft”. It is informing the user that the invoice is ready and must be paid. However, if you check the “FROM” field of the email, you see “[email protected]” which is almost same as an official “Microsoft Azure” email. This should make you suspicious of the sender and never click the links inside the mail. In addition, you see that if you hover the mouse above the link you discover that it is a different domain than an “azure.com” official website. So, you immediately understand that this email is scam and you must immediately delete it.
Another example of a Phishing email is below. Attacker pretends to be from Facebook and asks the user to click a link to update its login information. If you look again the “FROM” field of the email, you see “@facebookmail.com”. This email address is not from official Facebook address.
In case you are not observant, you could click the link provided in the email and then you will get directed to a malicious website. A fake Facebook website shown below can easily trick you to enter your details or download malware or virus. An example of a malicious Facebook website is shown below:
You can easily identify that website is phishing by looking that the Domain Name or URL (top row in the browser). Instead of showing the “facebook.com” domain, you see a long complex name “facebook.com.profile.id…..com” which tricks the user. Therefore, looking at the domain name of the website can help you understand that it is not the official Facebook website and you must close this page.
New Phishing techniques
As the years go by, new advanced techniques are developed. An example is Spear-Phishing, where attackers target specific businesses or people with powerful positions (executives, politicians etc.). Smishing, a combination of “SMS” and “phishing” words, it is a phishing attack that is delivered by using SMS texts. The latest type of phishing is called “Voice phishing” or “Vishing”. In a Vishing phone call, scammer tricks the user to disclose financial and personal information, including account numbers and passwords, using social engineering. Attackers or scammers usually claim that your account has been compromised, pose as a representative of police enforcement or your bank, or they may offer to assist you in installing software. So, if you receive a call from someone pretending to be from your bank or policy, remember that they will NOT ask you for credentials or private information.
4. Web Application Attacks:
Before exploring the attacks in the web applications, let’s see some basic information about web applications.
In the world of computer software, web apps or web applications are applications that run on the web (usually websites). There are also programs or software that run or are executed in mobiles and in desktop or PC. In any type of software, software developers try to write secure code and test the software before bringing it live to the users. However, as software becomes more complex, there is a possibility that a line in the software code is not well tested, and may cause unexpected behaviour or error. Usually, this is called a “software bug”.
Hackers are usually people trying to find those “software bugs”. If they find a way to use the “bug” or flaw and force the software to behave in an unexpected way, it is called “vulnerability”. Vulnerabilities can be used by attackers to have a variety of negative effects, such as changing or accessing undesired data. Therefore, hackers attempt discover vulnerabilities in order to take control not only of the application but of the whole server hosting the software. Vulnerabilities are growing and hackers exploit those vulnerabilities to attack the web apps and steal sensitive data or cause financial or reputational harm.
Attack surfaces
Coming back to web applications , the most common attack surface of a web app is the database. The database contains crucial information for the operation of the application as well as other interesting data. SQL Injection and Cross-Site scripting (XSS) attacks are two of the most well-known and dangerous threats. The former attack allows an attacker to interfere with the queries that application makes to the database. If it is a successful attack, hacker steals valuable information. In the XSS attack, the malicious actors try to exploit online applications’ forms or other input functionalities to inject malicious code and then, redirect users to malicious websites.
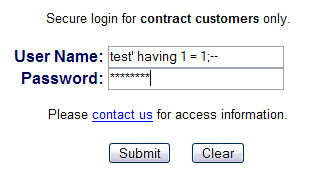
Vulnerable application
The image below demonstrates a malicious actor trying to discover if a web application is vulnerable to SQL injection. Basically, the hacker types special commands in the fields of username and password. Once submit button is clicked, those commands will be injected in the SQL query that web app will send to the database. If it is a vulnerable app, an error will appear and then, further actions will be taken to takeover the admin account.
5. Spam
In 1978, a marketing manager used ARPANET to send the first Spam email to 393 recipients. He was employed by the Digital Equipment Corporation, and it was promoting a new product. Despite the novelty of the concept, it was just as frustrating for the first 393 spam recipients as it is now.
Spam and Phishing campaigns are usually confused by the users. The difference is that spam is known as the delivery of unsolicited messages to a large mailing list while Phishing, as previously discussed, is using targeted social engineering method to steal user’s data. When spam is used as an attack vector to disseminate or enable other threats, it is regarded as a cybersecurity threat. For example, an attacker can use spam techniques to distribute a phishing email that contains malicious links to steal user’s data.
You can continue reading about the remaining cyber threats in Part II.


Pingback: Top 10 Cyber Threats (Part II) - CyberSecurity Learning by Phil
Pingback: Holiday Inn hotels hacked: Study - CyberSecurity Learning by Phil