Table of Contents
Real-world security architecture framework examples are surprisingly hard to find—most resources explain what frameworks are without showing how organizations actually implement them. After analyzing hundreds of security architecture deployments across IoT networks, financial services, healthcare, and manufacturing environments during my PhD research at the University of York, I’ve identified patterns in what works and what fails spectacularly.
Security architecture framework examples demonstrate how organizations structure their security controls, processes, and technologies using proven methodologies. The most widely adopted frameworks include SABSA (Sherwood Applied Business Security Architecture), the NIST Cybersecurity Framework, Zero Trust Architecture, and TOGAF with security extensions. Each framework provides different strengths—from business-driven approaches to technology-centric models—and understanding real implementation examples helps you choose the right approach for your situation.
In this guide, you’ll see concrete security architecture framework examples I’ve encountered in enterprise environments, including architecture diagrams, implementation decisions, and the messy reality that vendors omit from their sales materials. Whether you’re designing security architecture from scratch or improving existing frameworks, these real-world examples provide the practical clarity that theoretical documentation lacks.
Security Architecture Framework Examples: What They Actually Look Like in Practice
Before diving into specific frameworks, let’s establish what makes a security architecture framework valuable. At its core, a security architecture framework provides:
- Structured Methodology: A repeatable process for analyzing security requirements, designing controls, and evaluating effectiveness.
- Common Language: Standardized terminology that allows security professionals, IT teams, and business stakeholders to communicate effectively.
- Risk Management: Systematic approaches to identifying, assessing, and mitigating security risks aligned with business priorities.
- Compliance Mapping: Clear connections between security controls and regulatory requirements (GDPR, HIPAA, PCI-DSS, SOX).
- Implementation Guidance: Practical steps for translating abstract security principles into operational security controls.
The frameworks we’ll explore represent fundamentally different philosophical approaches. SABSA prioritizes business alignment, ensuring every security decision traces back to business objectives. NIST CSF emphasizes practical risk management with flexible implementation options. Zero Trust challenges traditional perimeter-based thinking by requiring continuous verification. TOGAF integrates security into broader enterprise architecture planning.
Understanding these differences matters because choosing the wrong framework for your organizational context leads to wasted effort, security gaps, and stakeholder frustration. Let me show you what each looks like in practice.
Security Architecture Framework Example #1: SABSA Implementation
What is SABSA?
The SABSA Institute developed SABSA (Sherwood Applied Business Security Architecture) as a business-driven framework that answers one fundamental question: “What security controls does the business actually need?”
SABSA operates on a six-layer matrix model that systematically addresses security from contextual business requirements down to operational components:
- Contextual Layer: Business view – What does the business need to protect?
- Conceptual Layer: Architect’s view – How should we organize security?
- Logical Layer: Designer’s view – What security services are required?
- Physical Layer: Builder’s view – What products and technologies implement these services?
- Component Layer: Tradesman’s view – How do we configure specific security components?
- Operational Layer: Facilities manager’s view – How do we operate and maintain security?
Real-World SABSA Example: Global Manufacturing Company
During an engagement with a multinational manufacturing organization, I witnessed a complete SABSA implementation that transformed their security posture from reactive to strategic. This security architecture framework example demonstrates SABSA’s power when implemented correctly.
The Business Context:
The company operated 47 manufacturing facilities across 23 countries, producing automotive components for major vehicle manufacturers. Their challenge: securing operational technology (OT) networks while maintaining 24/7 production availability. A security breach could halt production lines costing $1.2M per hour in lost production and contract penalties.
SABSA Implementation Approach:
Layer 1 – Contextual (Business Requirements):
The security team conducted stakeholder interviews with plant managers, production engineers, quality assurance, and executive leadership. They identified critical business requirements:
- Maintain 99.7% production uptime
- Protect intellectual property (manufacturing processes, formulas)
- Ensure product quality through secure quality control systems
- Comply with automotive industry security standards (ISO/SAE 21434)
- Enable remote monitoring without compromising plant security
These weren’t security requirements—they were business requirements that security needed to enable, not impede.
Layer 2 – Conceptual (Security Architecture):
Based on business requirements, architects defined security domains:
- Corporate IT network (office systems, ERP, email)
- Engineering network (CAD systems, product development)
- OT production network (PLCs, SCADA, HMI systems)
- Quality assurance network (measurement systems, inspection equipment)
- DMZ (remote access, vendor connections, data aggregation)
Each domain received a risk rating based on business impact. OT production networks were classified as “critical” due to production downtime costs. Engineering networks were “high risk” due to intellectual property value.
Layer 3 – Logical (Security Services):
Architects designed security services to protect each domain:
- Identity and access management: Role-based access control (RBAC) with segregation of duties
- Network security: Microsegmentation between security zones with stateful inspection
- Data protection: Encryption for data at rest (engineering files) and in transit (remote access)
- Threat detection: Behavioral monitoring for anomalous OT network activity
- Incident response: Tiered response with production-aware escalation
The critical innovation here was “production-aware” security. Rather than shutting down suspicious connections immediately (standard security response), the framework prioritized maintaining production while containing threats through isolation and monitoring.
Layer 4 – Physical (Technology Selection):
The team selected technologies that implemented logical security services:
- Industrial firewalls (Palo Alto OT Security) for network segmentation
- Privileged access management (CyberArk) for administrative access to critical systems
- OT-specific intrusion detection (Nozomi Networks) for behavioral analysis
- Secure remote access (Zero Trust Network Access) replacing VPN
- Security information and event management (Splunk) for centralized monitoring
Technology selection followed a “secure by design” principle—choosing products purpose-built for OT environments rather than adapting IT security tools.
Layer 5 – Component (Specific Configurations):
Engineers configured each technology according to defense-in-depth principles:
Industrial firewalls implemented application-aware rules. Rather than just “allow/deny” based on IP addresses and ports, rules understood industrial protocols (Modbus, OPC UA) and enforced protocol-specific security policies.
For example:
- HMI workstations could read PLC data but not write configuration changes
- Engineering workstations could upload new production programs only during maintenance windows
- Quality systems could receive measurement data but not control production equipment
This granular control prevented lateral movement even if an attacker compromised one system.
Layer 6 – Operational (Day-to-Day Management):
The security architecture framework example concluded with operational procedures:
- Change management: Security review required for all OT network changes
- Patch management: Risk-based patching during scheduled maintenance windows
- Monitoring: 24/7 SOC with OT-trained analysts
- Incident response: Production-aware playbooks with business impact assessment
- Continuous improvement: Quarterly architecture reviews with plant managers
The Results:
18 months after implementation:
- Zero production-impacting security incidents
- 97% reduction in security policy violations (mostly through better access controls)
- Remote monitoring enabled for all 47 plants (previously impossible due to security concerns)
- Passed automotive industry security audits (ISO/SAE 21434) on first attempt
- Estimated $8.2M in avoided breach costs and production downtime
Why This SABSA Example Worked:
The key to success was starting with business requirements, not security controls. Production managers weren’t told “we’re implementing security”; they were told “we’re solving your remote monitoring problem while protecting production.”
Every security decision traced back to a business requirement documented in the contextual layer. When conflicts arose (security vs. usability), the SABSA matrix provided a framework for resolution based on business priority, not security team preferences.
Security Architecture Framework Example #2: NIST Cybersecurity Framework in Action
Understanding the NIST CSF
The NIST Cybersecurity Framework organizes security activities into five core functions that map directly to operational security workflows: Identify, Protect, Detect, Respond, and Recover. Unlike SABSA’s business-first approach, NIST CSF provides a risk-based, operational model that organizations can implement incrementally.
The framework’s genius lies in its flexibility. Organizations self-assess their current state, define target states, and identify gaps without prescriptive technology requirements. This makes NIST CSF particularly valuable for organizations with resource constraints or varied security maturity across different business units.
Real-World NIST CSF Example: Regional Healthcare System
This security architecture framework example demonstrates NIST CSF implementation in a complex healthcare environment with 12 hospitals, 89 outpatient clinics, and approximately 15,000 employees.
The Healthcare Challenge:
Healthcare organizations face unique security architecture requirements:
- Life-critical systems that cannot be taken offline for security patches
- Massive attack surface (IoT medical devices, building systems, clinical workstations)
- Strict regulatory requirements (HIPAA, HITECH)
- Limited security budgets compared to financial services
- Highly distributed environments with minimal IT staff at satellite locations
The healthcare system had suffered a ransomware incident that encrypted administrative systems (fortunately not clinical systems). The board mandated comprehensive security improvement but provided limited additional budget.
NIST CSF Implementation:
Function 1 – Identify:
The security team began by inventorying assets and understanding business context:
Asset Management:
- 47,000+ network-connected devices catalogued
- 2,400 distinct medical device models (MRI, CT scanners, infusion pumps, patient monitors)
- 340 clinical applications
- 89 legacy systems running outdated Windows versions
Business Environment:
- Identified 23 “critical” clinical processes dependent on specific IT systems
- Mapped data flows for protected health information (PHI)
- Documented third-party dependencies (medical device vendors, cloud services, insurance partners)
Risk Assessment:
- Prioritized assets based on clinical impact, not just data sensitivity
- Ranked ransomware as highest probability, highest impact threat
- Identified legacy medical devices as greatest vulnerability (unpatched, unsupported)
This inventory revealed uncomfortable truths. Many medical devices ran embedded operating systems with known vulnerabilities that manufacturers refused to patch. Replacing these devices would cost $28M—budget that didn’t exist.
Function 2 – Protect:
The framework guided implementation of protective controls prioritized by risk:
Identity Management and Access Control:
- Implemented single sign-on (SSO) across clinical applications
- Required multi-factor authentication (MFA) for remote access and administrative accounts
- Created role-based access profiles aligned with clinical workflows
- Established privileged access management for administrative accounts
Data Security:
- Encrypted all laptop hard drives (BitLocker)
- Implemented database encryption for patient records
- Created data loss prevention policies blocking PHI transmission to unauthorized locations
Network Segmentation:
- Isolated medical devices on dedicated VLANs by device type and location
- Implemented microsegmentation between hospital departments
- Created secure remote access zones for vendor support
The key decision: rather than trying to secure unpatched medical devices directly, they isolated these devices through network segmentation and monitoring, accepting residual risk with compensating controls.
Function 3 – Detect:
Detection capabilities focused on behavioral anomalies rather than signature-based detection:
Continuous Monitoring:
- Deployed endpoint detection and response (EDR) on all workstations
- Implemented network traffic analysis for medical device networks
- Created SIEM correlation rules specific to healthcare attacks
Anomaly Detection:
- Established behavioral baselines for medical devices (predictable communication patterns)
- Monitored for unauthorized network scanning
- Tracked privileged account usage
Security Continuous Monitoring:
- Automated vulnerability scanning
- Configuration compliance checks
- Dark web monitoring for stolen healthcare credentials
They discovered that most medical devices have very predictable network behavior. An infusion pump talks to the pharmacy system, the EHR, and its monitoring console—that’s it. Any deviation triggers investigation.
Function 4 – Respond:
The healthcare system developed tiered response procedures prioritizing patient safety:
Response Planning:
- Created “clinical impact assessment” as first step in any incident response
- Defined clear escalation paths to clinical leadership for patient safety decisions
- Established communication templates for different incident types
Incident Response Playbooks:
- Ransomware: Isolate affected segments, assess clinical impact, activate paper chart procedures if needed
- Data breach: HIPAA breach notification procedures, patient communication plans
- Medical device compromise: Clinical engineering involvement, vendor notification
Response Coordination:
- Integrated clinical engineering team into security incident response
- Created “security liaison” roles in each hospital (clinical staff with security training)
- Conducted tabletop exercises simulating clinical impact scenarios
The novel approach: clinical staff participated in security incident response planning, ensuring patient safety considerations weren’t afterthoughts.
Function 5 – Recover:
Recovery planning focused on resuming clinical operations, not just restoring IT systems:
Recovery Planning:
- Identified critical clinical systems requiring priority recovery
- Created offline backup systems for life-critical applications
- Documented “downtime procedures” for operating without IT systems
Recovery Procedures:
- Prioritized recovery sequence based on clinical needs (ER systems before billing systems)
- Validated restore procedures through quarterly testing
- Created degraded-mode operations plans (paper charts, manual medication administration)
Communication:
- Patient communication plans for breach notification
- Staff training on downtime procedures
- Clinical leadership briefing templates
Improvement:
- Post-incident reviews including clinical staff
- Integration of lessons learned into security architecture
- Regular security posture assessment against evolving threats
The Results:
24 months after NIST CSF implementation:
- Detected and contained ransomware attempt before encryption (saved estimated $12M)
- Achieved HIPAA Security Rule compliance
- Passed external security assessment with zero critical findings
- Reduced security incidents by 73%
- Maintained zero patient safety incidents related to security controls
Why This NIST CSF Example Succeeded:
The framework’s five functions mapped naturally to healthcare operations. Clinical staff understood “Identify, Protect, Detect, Respond, Recover” in the context of patient care—they already used these concepts for infection control and medical emergencies.
NIST CSF’s flexibility allowed prioritizing patient safety over security dogma. When security controls conflicted with clinical workflows, the framework provided structure for documenting risk acceptance decisions based on business (clinical) priorities.
The incremental implementation approach meant the healthcare system didn’t need $50M upfront. They implemented controls progressively, demonstrating value and building stakeholder trust before requesting additional resources.
Security Architecture Framework Example #3: Zero Trust Architecture Implementation
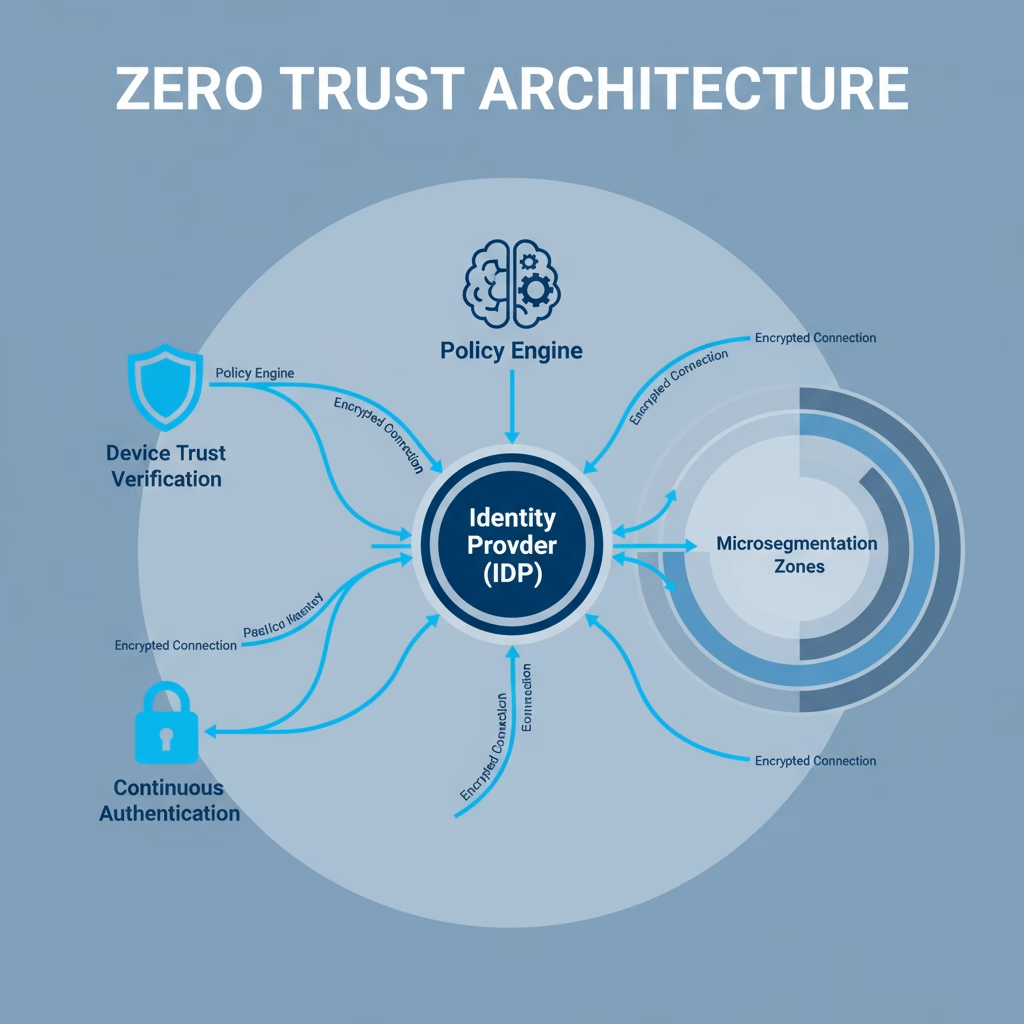
What Makes Zero Trust Different
Zero Trust represents a paradigm shift from perimeter-based security. Traditional security architecture assumes everything inside the network perimeter is trustworthy. Zero Trust assumes breach and requires continuous verification of every access request regardless of location.
The core tenets of Zero Trust architecture:
- Verify explicitly: Authenticate and authorize based on all available data points
- Use least privilege access: Grant minimum required access, just-in-time
- Assume breach: Minimize blast radius and segment access
This security architecture framework example demonstrates Zero Trust principles in a modern cloud environment.
Real-World Zero Trust Example: Financial Technology Startup
A rapidly scaling fintech startup faced security challenges inherent to modern organizations: distributed workforce, cloud-native infrastructure, multiple SaaS applications, and minimal security team.
The Fintech Context:
- 280 employees across 17 countries (fully remote)
- Customer-facing payment processing platform (PCI-DSS required)
- AWS-based microservices architecture
- Integration with 47 third-party financial APIs
- 14-person engineering team with DevOps culture
- 2-person security team (1 full-time, 1 contractor)
Traditional VPN architecture wouldn’t scale. Employees needed access to production systems from home offices, coffee shops, and coworking spaces worldwide. Network perimeter didn’t exist in any meaningful sense.
Zero Trust Implementation:
Identity as the Perimeter:
Rather than network-based access control, the fintech implemented identity-based perimeter:
Identity Provider (Okta):
- Single source of identity for all employees, contractors, and service accounts
- Multi-factor authentication required (hardware keys for production access)
- Risk-based authentication (unusual location triggers additional verification)
- Automated offboarding (disable all access instantly when employment ends)
Every access decision started with: “Who is this user, and can we verify their identity?”
Device Trust:
Not all devices deserved equal access. The security architecture framework example implemented device posture checks:
Managed Devices (Company-Issued Laptops):
- Full disk encryption required
- Endpoint detection and response agent installed
- Automatic security updates enforced
- Configuration compliance validated before granting access
Unmanaged Devices (Personal Devices, Partner Systems):
- Limited access to specific applications only
- No local data caching
- Enhanced monitoring and logging
- Session timeout after 2 hours
Engineers using personal laptops for development could access non-production environments but not customer data or production infrastructure.
Application-Level Access Control:
Instead of granting network access, the architecture provided application-level access:
Software-Defined Perimeter:
- Applications invisible to unauthorized users (no DNS resolution, no network response)
- Direct encrypted connection from user device to application (no VPN)
- Access granted per-application based on user identity and device trust
- Automatic revocation when conditions change
An engineer approved for read access to production databases could only connect to databases, not web servers, load balancers, or other infrastructure—even though all ran in the same AWS VPC.
Microsegmentation:
Cloud-native architecture enabled granular microsegmentation:
Service-to-Service Communication:
- Every microservice had cryptographic identity (AWS IAM roles)
- Service mesh (Istio) enforced mutual TLS between services
- Authorization policies defined which services could communicate
- Network policies blocked unauthorized service-to-service traffic
The payment processing service could call the fraud detection service but not the email notification service. Compromise of one microservice couldn’t cascade across the entire platform.
Continuous Monitoring and Risk Assessment:
Zero Trust architecture requires continuous verification:
User and Entity Behavior Analytics (UEBA):
- Behavioral baselines for each user (typical working hours, accessed applications)
- Anomaly detection (access from new country, unusual data volume)
- Risk scoring combining multiple signals (impossible travel, failed auth attempts)
- Automated response (force re-authentication, alert security team, temporary suspension)
Logging and Audit:
- Every access request logged (who, what, when, where, device, outcome)
- Centralized logging for security investigation
- Real-time alerting for high-risk activities
- Retention for compliance requirements
The Results:
18 months after Zero Trust implementation:
- Passed PCI-DSS assessment with zero critical findings
- Detected and prevented insider threat (disgruntled employee attempting data exfiltration)
- Enabled GDPR-compliant remote work across EU
- Eliminated VPN-related helpdesk tickets (previously 12% of all tickets)
- Reduced mean time to provision access from 48 hours to 15 minutes
Why This Zero Trust Example Worked:
The fintech’s cloud-native architecture made Zero Trust implementation natural. Without on-premises infrastructure or network perimeter to defend, identity-based controls were simpler than traditional perimeter security.
The DevOps culture embraced “security as code.” Authorization policies lived in Git repositories, reviewed like application code, and automatically deployed through CI/CD pipelines.
Zero Trust actually improved developer productivity. Rather than VPN complexities, developers accessed only what they needed through simple SSO. The security team removed obstacles while strengthening security.
Comparing Security Architecture Framework Examples
| Framework | Best For | Implementation Time | Complexity | Cost | Business Alignment |
|---|---|---|---|---|---|
| SABSA | Business alignment, large enterprises, complex organizations | 18-36 months | High | $$$ | Excellent |
| NIST CSF | Risk management, practical implementation, incremental improvement | 6-12 months | Medium | $$ | Good |
| Zero Trust | Cloud environments, distributed workforce, modern architectures | 24-48 months | High | $$$ | Medium |
| TOGAF | Enterprise architecture integration, IT transformation | 12-24 months | High | $$$ | Good |
| ISO 27001 | Compliance, certification requirements | 12-18 months | Medium | $$ | Medium |
Choosing the Right Framework
The security architecture framework examples I’ve shared reveal that framework selection depends on organizational context:
Choose SABSA if:
- You need security investments justified by business value
- Organization has complex business requirements
- Multiple stakeholders with competing priorities
- Enterprise-scale with budget for comprehensive architecture
- Security must align with business strategy
Choose NIST CSF if:
- You need practical, actionable security improvements now
- Organization has limited security maturity
- Budget constraints require incremental investment
- Need flexibility across diverse business units
- Want to demonstrate quick wins to build stakeholder support
Choose Zero Trust if:
- You’re building or migrating to cloud infrastructure
- Workforce is distributed or remote
- Traditional network perimeter doesn’t exist
- Security team is small relative to infrastructure size
- You embrace DevOps and infrastructure-as-code
Choose TOGAF if:
- Security is part of broader enterprise architecture initiative
- Organization is undergoing IT transformation
- Need integration between security architecture and other IT architectures
- Enterprise architecture team already exists
Choose ISO 27001 if:
- Certification is business requirement (customer contracts)
- Operating in highly regulated industry
- Need documented, auditable security processes
- Want internationally recognized security posture
Many organizations implement hybrid approaches. A common pattern combines NIST CSF (operational security) with elements of SABSA (business alignment) and Zero Trust principles (cloud security).

Implementation Best Practices for Security Architecture Frameworks
Regardless of which framework you choose, certain implementation practices consistently lead to success. These lessons come from analyzing dozens of security architecture framework examples across diverse industries.
Start with Business Context, Not Technology
The most common failure pattern I’ve observed: organizations jump directly to selecting security tools without understanding what they’re protecting and why it matters to the business.
The Right Approach:
Begin by answering fundamental questions:
- What assets have the highest business value?
- What business processes depend on these assets?
- What would business impact look like if these assets were compromised?
- What regulatory requirements apply?
- What risk level can the business accept?
A financial services client learned this lesson painfully. They invested $3M in a sophisticated security monitoring platform before mapping their critical data flows. The monitoring platform detected thousands of alerts, but analysts couldn’t prioritize effectively because they didn’t know which systems mattered most to the business. They ended up spending another $500K on consultants to conduct the business impact analysis they should have done first.
Document Architecture Decisions and Rationale
Security architectures evolve over time. People change roles. Technologies get replaced. Six months after implementation, nobody remembers why certain design decisions were made.
Essential Documentation:
Architecture Principles: The guiding rules that inform all decisions
Design Decisions: What choices were made and why alternatives were rejected
Risk Acceptance: What risks were knowingly accepted and by whom
Technology Rationale: Why specific products were chosen
Implementation Roadmap: Phased approach with dependencies and timelines
I maintain architecture decision records (ADRs) for every significant choice. These short documents answer: What was decided? Why? What alternatives were considered? What are the consequences? This saved countless hours when auditors asked “why isn’t encryption required for internal traffic?” We pointed to ADR-047 explaining the decision to accept risk for internal networks based on physical security controls and monitored network boundaries.
Implement Incrementally with Measurable Milestones
The security architecture framework examples that succeeded all shared incremental implementation approaches. Those that failed attempted “big bang” transformations.
Effective Phasing Strategy:
Phase 1 – Quick Wins (Months 1-3):
- Implement controls with immediate impact and low disruption
- Generate early success stories to build stakeholder support
- Examples: MFA for remote access, security awareness training, vulnerability scanning
Phase 2 – Foundation (Months 4-9):
- Deploy core architectural components
- Establish security operations capabilities
- Examples: SIEM platform, identity management, network segmentation
Phase 3 – Integration (Months 10-18):
- Connect security controls and enable automation
- Mature security operations processes
- Examples: Automated incident response, security orchestration, threat intelligence integration
Phase 4 – Optimization (Months 19+):
- Refine based on lessons learned
- Advance maturity of security capabilities
- Examples: Behavioral analytics, threat hunting, continuous improvement
Each phase delivers tangible security improvements. Stakeholders see value before committing to the next phase. This builds momentum and trust.
Measure and Communicate Effectiveness
Security architecture framework examples that gained long-term executive support all demonstrated measurable value.
Effective Security Metrics:
Risk Reduction Metrics:
- Critical vulnerabilities reduced by X%
- Mean time to detect incidents decreased from Y to Z
- Percentage of assets meeting security baselines
Operational Metrics:
- Security incidents handled within SLA
- Security control availability
- Time to provision access
Business Impact Metrics:
- Avoided breach costs through early detection
- Compliance audit findings reduced
- Customer trust improvements (NPS scores)
Avoid “vanity metrics” like number of alerts processed or gigabytes of logs collected. These don’t demonstrate value to business stakeholders.
A manufacturing client I worked with tracked “production uptime protected by security controls.” Every quarter, they calculated production hours that would have been lost to security incidents if controls hadn’t prevented or contained them. This metric resonated with operations executives in a way that “99.7% control availability” never did.
Plan for Architecture Evolution
Security threats evolve. Business requirements change. Technologies advance. Static security architectures fail.
Build Evolution Mechanisms:
Regular Architecture Reviews:
- Quarterly: Tactical adjustments based on threat intelligence
- Annual: Strategic architecture assessment
- Ad-hoc: Triggered by major business changes or security events
Threat Intelligence Integration:
- Subscribe to relevant threat intelligence feeds
- Participate in information sharing communities
- Adjust architecture based on emerging threat patterns
Technology Refresh Cycles:
- Track technology lifecycle
- Plan upgrades before products reach end-of-life
- Evaluate emerging technologies for architectural fit
Continuous Validation:
- Penetration testing validates controls effectiveness
- Red team exercises test detection and response
- Tabletop exercises validate processes
The security architecture framework examples that remained effective over years all included formal evolution processes. Those that ossified into unchanging documentation became irrelevant within 18-24 months.
Common Pitfalls in Security Architecture Implementation
Pitfall #1: Copying Templates Without Customization
Security architecture templates and reference architectures provide valuable starting points. But directly copying them without customization leads to architectural mismatch.
The Problem:
I’ve seen organizations implement NIST CSF exactly as documented in case studies without considering their specific business context. A healthcare provider copied a financial services security architecture, resulting in overly restrictive controls that interfered with clinical workflows and controls that didn’t address healthcare-specific risks (medical device security, HIPAA requirements).
The Solution:
Use frameworks and examples as inspiration, not blueprints. Customize based on:
- Your specific business processes and workflows
- Your industry’s unique threats and compliance requirements
- Your organization’s risk tolerance
- Your current technology stack and constraints
- Your security team’s capabilities
Pitfall #2: Technology-First Approach
Organizations frequently start by selecting security products, then try to fit them into an architecture.
The Problem:
This leads to security tools that don’t integrate well, redundant capabilities, gaps in coverage, and tools that solve problems you don’t have while ignoring problems you do have.
The Solution:
Define architectural requirements first:
- Identify security capabilities needed (authentication, encryption, monitoring, etc.)
- Specify integration requirements (what needs to work together)
- Document constraints (budget, existing infrastructure, skills)
- Then evaluate technologies that meet these requirements
Technology selection is the output of architecture design, not the input.
Pitfall #3: Ignoring Operational Reality
Beautiful architecture diagrams that don’t account for operational constraints fail in production.
The Problem:
An architecture requiring 24/7 security operations center when the organization only has security staff during business hours. Controls that require expertise the team doesn’t possess. Processes that assume response times the organization can’t meet.
The Solution:
Design architecture based on realistic operational capabilities:
- What skills does the team actually have?
- What response times can realistically be achieved?
- What level of operational maturity exists?
- What budget is available for ongoing operations?
If the architecture requires capabilities the organization lacks, either build those capabilities first or design compensating controls that work within constraints.
Pitfall #4: Analysis Paralysis
Some organizations spend years analyzing and planning security architecture without implementing anything.
The Problem:
Perfect architecture doesn’t exist. Waiting for perfect understanding or perfect alignment leads to never starting. Meanwhile, security risks remain unaddressed.
The Solution:
Embrace iterative implementation:
- Start with a “good enough” architecture based on current understanding
- Implement incrementally
- Learn from each phase
- Refine architecture based on lessons learned
Done is better than perfect. Especially in security, where every day without controls represents accumulating risk.
Pitfall #5: Treating Architecture as One-Time Project
Organizations complete security architecture projects, document everything beautifully, then file it away and never revisit it.
The Problem:
Security architecture becomes outdated rapidly. Within 12 months, the architecture documentation no longer reflects reality. New technologies get deployed without architectural review. The architecture becomes historical documentation rather than living guidance.
The Solution:
Establish architecture governance:
- Architecture review required for significant changes
- Regular architecture refresh cycles
- Architecture integrated into change management processes
- Metrics tracking architecture compliance
Architecture is a continuous discipline, not a deliverable.
Essential Skills for Security Architecture
For professionals interested in security architecture careers, understanding required competencies helps focus skill development.
Technical Foundation
Network Architecture and Protocols:
Deep understanding of network fundamentals (TCP/IP, routing, switching) and how security controls integrate with network infrastructure. Cloud networking (VPC, subnets, security groups) increasingly important.
Security Technologies:
Broad knowledge across security domains: identity and access management, encryption, network security, endpoint security, application security, cloud security. Not expert-level depth in everything, but sufficient understanding to architect integrated solutions.
Enterprise Architecture:
Understanding of how IT systems interconnect. Knowledge of enterprise architecture frameworks (TOGAF, Zachman). Ability to position security within broader IT architecture initiatives.
Systems Thinking:
Ability to understand complex systems with many interacting components. Recognizing how changes in one area create effects elsewhere. Understanding feedback loops and unintended consequences.
Business and Communication Skills
Business Acumen:
Understanding how organizations create value. Ability to translate security requirements into business language. Familiarity with financial concepts (ROI, total cost of ownership, budget planning).
Stakeholder Management:
Working effectively with diverse stakeholders: technical teams, business leaders, auditors, executives. Understanding their different perspectives and priorities. Building consensus across competing interests.
Risk Communication:
Explaining technical risks in business terms. Quantifying security risks in ways business leaders can evaluate. Presenting risk/reward tradeoffs for security decisions.
Technical Writing:
Creating clear architecture documentation. Writing decision rationale that future architects can understand. Documenting complex concepts for diverse audiences.
Strategic and Analytical Skills
Threat Modeling:
Systematically analyzing potential attack vectors. Understanding attacker motivations and capabilities. Anticipating security weaknesses before they’re exploited.
Requirements Analysis:
Extracting security requirements from business objectives, compliance mandates, and risk assessments. Identifying conflicts between requirements and designing approaches to resolve them.
Strategic Planning:
Developing multi-year security architecture roadmaps. Balancing short-term needs with long-term vision. Planning technology evolution and obsolescence.
Analytical Thinking:
Breaking complex problems into manageable components. Evaluating multiple solution alternatives. Making decisions based on incomplete information.
Practical Experience
The security architecture framework examples I’ve shared illustrate why hands-on experience matters. You can’t learn security architecture purely from books or certifications. You need exposure to:
- Failed implementations (learning what doesn’t work)
- Architectural decisions under constraint (budget limits, timeline pressure, skill gaps)
- Stakeholder conflicts and resolution
- Technology integration challenges
- Architecture evolution as requirements change
This typically requires 7-10 years in security roles before transitioning to architecture. The most effective security architects I know have backgrounds spanning multiple security domains (network security, application security, cloud security) plus experience outside security (development, operations, business analysis).
Frequently Asked Questions About Security Architecture Frameworks
What is the difference between security architecture and security engineering?
Security architecture focuses on the “what” and “why”—what security capabilities are needed and why they’re necessary to manage organizational risk. Security engineering focuses on the “how”—how to implement and operate those security capabilities.
An architect designs that a network requires segmentation between production and development environments with specific traffic controls. An engineer configures the firewall rules and network access control lists that implement that segmentation.
Both roles are critical. Architecture without engineering remains theoretical. Engineering without architecture risks implementing security controls that don’t address actual business risks or integrate poorly with the broader environment.How long does it take to implement a security architecture framework?
Implementation timelines vary dramatically based on organization size, current security maturity, chosen framework, and available resources. Based on the security architecture framework examples I’ve shared:
Small organization (under 500 employees), starting from low maturity: 6-12 months for initial implementation
Mid-size organization (500-5,000 employees), moderate maturity: 12-24 months
Large enterprise (5,000+ employees), complex environment: 24-48 monthsThese timelines represent reaching a functional security architecture, not “complete” implementation. Security architecture evolves continuously—you’re never truly “done.”
Organizations that attempt faster implementation typically cut corners that create vulnerabilities or stakeholder resistance. Those that move too slowly often lose executive support before demonstrating value.Can small organizations use enterprise security architecture frameworks?
Absolutely, but with appropriate scaling. The security architecture framework examples from large enterprises provide useful patterns that small organizations can adapt.
The key is focusing on principles rather than attempting comprehensive implementation. A small organization implementing SABSA wouldn’t create the full six-layer matrix with extensive documentation. Instead, they’d document business requirements, map security controls to those requirements, and establish basic architecture governance.
Similarly, a small organization adopting NIST CSF might focus on Identify and Protect functions initially, establishing basic security hygiene, then gradually adding Detect, Respond, and Recover capabilities as resources permit.
Small organizations benefit from lightweight, pragmatic implementations that provide structured thinking without bureaucratic overhead.Which security architecture framework is best for cloud environments?
Cloud environments favor architectures emphasizing identity over network perimeter, which makes Zero Trust particularly well-suited. However, successful cloud security architecture often combines multiple frameworks:
Zero Trust provides principles for cloud-native access control, eliminating reliance on network perimeter that doesn’t exist in cloud environments.
NIST CSF offers practical risk management structure that works across hybrid cloud and on-premises environments.
Cloud-specific frameworks from providers (AWS Well-Architected Framework, Azure Security Benchmark, Google Cloud Security Foundations) provide detailed implementation guidance for specific platforms.The security architecture framework examples in cloud environments typically implement Zero Trust principles using cloud-native services, structured according to NIST CSF functions, and measured against cloud provider security benchmarks.
Conclusion: Learning from Real Security Architecture Framework Examples
The security architecture framework examples I’ve shared—from SABSA’s business-driven manufacturing implementation to NIST CSF’s healthcare deployment and Zero Trust’s cloud-native fintech approach—demonstrate that successful security architecture requires matching framework strengths to organizational context. Organizations implementing frameworks as rigid templates typically struggle, while those adapting principles to their specific needs succeed.
Real security architecture framework examples reveal consistent patterns: clear business alignment, realistic timelines, incremental deployment, and continuous refinement. No single framework solves all problems. SABSA excels at business alignment but demands significant documentation. NIST CSF provides practical risk management with flexible guidance. Zero Trust addresses modern threats but requires multi-year transformation. TOGAF integrates with enterprise architecture but assumes organizational maturity.
The most effective approach combines frameworks—using NIST CSF for program structure, Zero Trust for technical architecture, SABSA for stakeholder communication, and ISO 27001 for compliance. These security architecture framework examples demonstrate that effective security requires balancing rigor with pragmatism, aligning controls with business objectives, and creating architectures that evolve with changing threats.
You can start with clear business context, choose frameworks matching your needs, implement incrementally with measurable milestones, and treat architecture as continuous discipline rather than one-time project.
Ready to implement security architecture frameworks? Start by understanding network security authentication functions and build from there.
References
- https://seraphicsecurity.com/learn/zero-trust/zero-trust-architecture-in-2025-7-key-components/
- https://www.nccoe.nist.gov/projects/implementing-zero-trust-architecture
- https://securityscorecard.com/blog/what-is-zero-trust-architecture-9-steps-to-implementation/
- https://www.pomerium.com/blog/zero-trust-architecture-examples-with-actionable-guide
- https://www.carahsoft.com/blog/palo-alto-networks-from-concept-to-implementation-operationalizing-zero-trust-architecture-in-government-environments-blog-2025
- https://www.helpnetsecurity.com/2025/06/13/zero-trust-implementation-guide/
- https://www.apono.io/blog/how-to-implement-zero-trust/
- https://ntgit.com/zero-trust-architecture-in-2025-shifting-from-perimeter-security-to-never-trust-always-verify/
- https://www.isms.online/zero-trust/guide-on-implementing-zero-trust-in-your-organisation/
- https://www.microsoft.com/en-us/security/business/zero-trust