
10 Ways To Protect yourself from Hackers. In this post, you will find some simple methods that everyone can follow to stay protected against hackers.
Best Methods To Protect Yourself
There are many tips and tricks that you can do to improve the security of your accounts and your computer. Our focus will be the protection of user accounts and how to avoid being infected. However, there is no method to guarantee 100% protection. These methods can be followed to help you minimize the risk of getting hacked. Moreover, in case you become a victim, having a security measure in place will make things harder for the hacker to carry on the attack. Apart from that, some methods will help you recover faster and easier in the worst cases.
So, what are the most important tips for staying safe online? Here is the list :
10 ways to protect yourself from hackers :
1) Use Strong Passwords (Make things difficult for Hackers)
The first rule is to always use a STRONG password.
What we mean by strong? In simple words, you must not have a “123456” or “helloworld” as a password. Other examples are:
- 123456 (or any chronologically-ordered numbers)
- 987654321
- 123123
- QWERTY
- 111111
- password
Those password examples must be avoided.
A strong password means to be at least six characters in length, usually eight to ten are preferable, and to contain mix of characters (i.e., letters, numbers, symbols, upper/lower case). You must avoid using simple words, names, dates or other formats that hackers can easily guess.
A simple trick to memorize a complex password is the following; Use the first letter of each word in a favorite quote, capitalize every other letter, and add a number. For instance, “I love going to the beach for swimming” becomes the password “iLgTtBfS1!”.
There can find other creative ways to create complex password in this link.
2) Enable Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is a type of electronic authentication in which a user is only allowed access to a website or application after successfully demonstrating two or more forms of identification, such as knowledge, possession, and inherence, to an authentication system. Enabling this feature will be protect your account from being accessed by an individual without your consent.
There are many mobile apps, including Duo or Authenticator, which help users enable 2-Factor Authentication. Those apps have integrations with many social media sites (and not only). Authentication apps allow you to review and approve or not every login attempt to your account. In this way, you know when a login attempt occurs. Try it and you will know every login attempt to your accounts
3) Avoid Opening Emails From Strangers/Hackers
As a second best practice to follow is to avoid opening emails from unknown senders. Usually, hackers try to imitate and spoof the email addresses of known contacts. However, if you are careful and pay attention to the sender’s email address or writing style of the email, you can discover that the sender is a stranger.
If you notice something suspicious in the email, immediately delete it and never download or open any attachment. There is the risk of downloading a virus or malware from an unknown email. As explained in our posts Part I and Part II, attackers try to find new ways to spread malicious software via spam email. Therefore, a good tip is to be suspicious every time you open a new email.
4) Update Your Software
It is important to keep your devices, both personal computers and mobiles, up-to-date with the latest software!
Why? Because vulnerabilities exist, and companies run behind hackers to fix those bugs. So, most vendors publish an updated version of the software to fix the vulnerabilities and stop exploitation.
Users should always try to have their computer software updated. In this way, you minimize the risk of being actively exploited and hacked by someone. If you don’t keep your devices updated, at the same time you are insecure. Hackers try to exploit vulnerable software to access computers and steal sensitive information.
So, try to enable auto-update in your software.
5) Avoid Using Public WiFi
I am sure that you have already seen this point in a security blog. Using public WiFi involves security risks that people might be unaware.
For example, a malicious actor may create a fake WiFi station without requiring password to connect. Your device, automatically sometimes, will scan the networks and connect to the fake WiFi as it it does not ask for a password. At that moment, the malicious actor will be able to intercept your connection and access the data that your device sends to the internet. Therefore, any passwords or personal information sent by the device during internet browsing will be stolen by the malicious person without leaving any traces.
The above scenario briefly explains that connecting to public WiFi might be a trap to steal your information.
6) Take Frequent Backups
Taking a backup is not an obvious prevention step to stay protected but it is vital for recovering your system and data.
Imagine getting infected with a ransomware or virus that encrypts your data. You will have no choice to recover it unless you pay the ransom (sometimes files are not recoverable) or you have a backup. For this reason, taking a backup of your files and system frequently can save you time!!
7) Use Antivirus and Antimalware Software
It is obvious that any user that has a device connected to the internet must have antivirus and antimalware software.
As explained and in our previous articles, scanning your device with an antivirus will help to detect and deteriorate any viruses. Not only you protect your files, but also you keep your system healthy and fast. Removing unwanted files and especially executable files downloaded from unofficial sources will protect you from getting infected.
There are many free and paid solutions to protect a single or multiple devices. A single Google search will help you to find a protection solution.
8) Use Windows/Linux Firewall To Stop Hackers
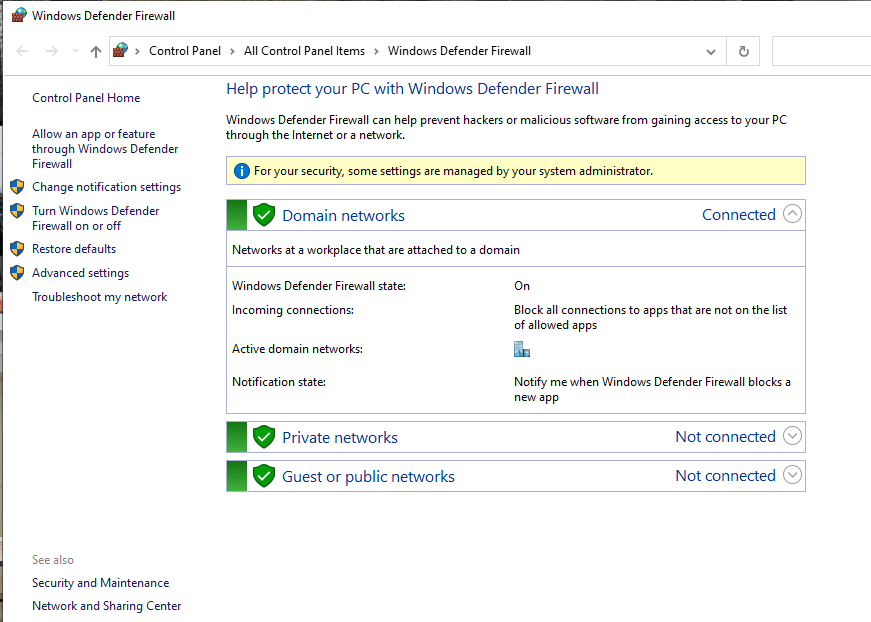
If you are not aware, Windows and Linux machines have built-in firewall. A firewall is a network security system that monitors and controls incoming and outgoing network traffic of your system based on some security rules.
By default, the firewall is enabled in both Operating Systems (OS) but in case you see an error that it is disabled, please enable it.
There are some cases where malicious software try to connect to the internet and the firewall blocks these requests. That’s why it is a good option to add an extra security to your device.
9) Install Browser Security Extensions
A small advice to keep you safe while browsing is to install security extension to your browser, Chrome/Edge/Firefox.
There are many free security tools that can be installed in your browser that scan websites and attempt to stop malicious scripts or phishing websites.
Usually, those tools are installed along with antivirus or antimalware, but in any case try to use one.
10) Visit Only HTTPS Websites
Nowadays, very few websites are not using encryption. To ensure that you are safe, there are two things to look for;
1) a “lock” symbol will appear on the left of the address bar, and 2) an “https” text will appear in front of the domain name. Those two things are shown below.
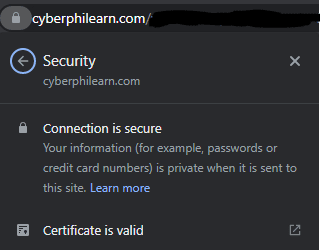
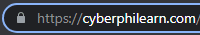
If you are visiting a website that doesn’t have a lock in front of the domain name, try to avoid it. Especially any financial institute that doesn’t have HTTPS it should be avoided as they might be phishing websites.
To explain what actually mean the above signs, they show that content transfered between your computer and the website is encrypted. Data including credit card number, personal information and other confidential data are encrypted so noon can intercept the connection and steal them.
That is the reason that you must browse only secure websites that actually care about your safety.
