Table of Contents
Whether you are a student, an IT administrator looking to pivot, or a developer seeking security expertise, this How to Become a Penetration Tester: 2026 Career Guide is your blueprint.
The cybersecurity job market is facing a paradox. On one side, headlines scream about a talent shortage of nearly 4 million professionals. On the other, junior applicants struggle to land their first interview. Why the disconnect?
Analysis of industry hiring trends reveals the answer: Companies are not looking for tool-users; they are looking for problem solvers who understand the architecture of the systems they break.
If you are struggling to navigate the maze of certifications, conflicting advice, and gatekeeping, you are not alone. This guide is designed to cut through the noise. We have curated data from industry frameworks, analyzed successful career trajectories, and simplified the technical roadmap.
Understanding the Core Concepts
Before diving into tools and operating systems, we must define the battlefield. A common misconception among newcomers is that penetration testing is solely about “hacking in.” Reality is far more structured.
The Definition: Assessment vs. Exploitation
To understand the role, you must distinguish between three distinct activities often conflated in job descriptions.
- Vulnerability Assessment (VA): This is a broad, automated sweep. You use scanners to identify known flaws (like an outdated Apache server). It is wide but shallow.
- Penetration Testing (PT): This is where human intelligence applies. You take the vulnerabilities found in the VA phase and attempt to exploit them to prove impact. It is targeted and deep.
- Red Teaming: This is a simulation of a specific adversary. The goal isn’t just to find bugs, but to test the organization’s response capabilities (Blue Team).
Analyst Note: The 2026 market demands professionals who can do more than run a Nessus scan. The highest-paid testers are those who can chain minor vulnerabilities together to demonstrate a critical business risk.
The Methodologies
Professional pentesting is not chaos; it is a rigid process. To be hired, you must demonstrate familiarity with industry standards.
- PTES (Penetration Testing Execution Standard): The bible of the industry. It covers everything from pre-engagement interactions to reporting.
- OSSTMM (Open Source Security Testing Methodology Manual): Focuses on operational security and metrics.
- OWASP (Open Web Application Security Project): The gold standard for web applications. If you are testing websites, you live and breathe the OWASP Top 10.
The “Why” Over the “How”
Tools change. In 2020, everyone used one set of scripts; by 2026, AI-assisted tooling will dominate. If you only learn how to type a command, you will become obsolete. If you learn why a buffer overflow occurs or why an SQL injection works, you can adapt to any tool.
So, why does this matter? Because in a technical interview, you won’t be asked to run a tool. You will be asked to explain the TCP 3-way handshake or how Kerberos authentication tickets are generated.
Key Differences Analyzed: The 2026 Roadmap
We analyzed thousands of job postings and forum discussions to identify the specific skills that separate successful applicants from the resume pile. Here is the breakdown of the critical competencies.
Phase 1: The Non-Negotiable Foundations
You cannot hack what you do not understand. The most common failure point for aspiring testers is skipping the basics to jump straight to Kali Linux.
| Skill Domain | Why It Matters | Key Concepts to Master |
|---|---|---|
| Networking | The internet is built on packets. You need to know how they move. | TCP/IP, Subnetting, OSI Model, DNS, HTTP/HTTPS, Ports & Protocols. |
| Linux | 90% of security tools run on Linux. You must be comfortable in the terminal. | File permissions (chmod/chown), Bash piping, Grep/Sed/Awk, Process management. |
| Windows/AD | Corporate environments run on Active Directory (AD). | Domain Controllers, Kerberos, LDAP, Group Policy, NTLM hashing. |
Community Insight: Discussions in security communities frequently highlight that while Linux is fun, Active Directory exploitation is where the money is. Most enterprise breaches happen because of misconfigured Windows domains, yet many juniors ignore this skill.
Phase 2: Programming and Scripting
Do you need to be a developer? No.
Do you need to read code? Absolutely.
In 2026, the ability to read Python or Bash scripts and modify them on the fly is essential. Automation is king. You don’t need to build a software application from scratch, but you must be able to:
- Read an exploit script to ensure it’s safe (and not a trap).
- Modify a payload to bypass a specific filter.
- Write simple automations to save time during an engagement.
Recommended Languages:
- Python: The lingua franca of security.
- Bash: For automating Linux tasks.
- PowerShell: Critical for Windows/Active Directory attacks.
Phase 3: The Toolset
While tools are secondary to knowledge, proficiency is expected. Here are the industry standards you will encounter.
- Network Scanning: Nmap (The cartographer of the network).
- Web Proxy: Burp Suite Pro (The industry standard for web app testing).
- Exploitation: Metasploit (Great for learning, used sparingly in advanced tests).
- Password Cracking: Hashcat and John the Ripper.
- Active Directory: BloodHound (Visualizing attack paths).
The Certification Landscape: Where to Invest?
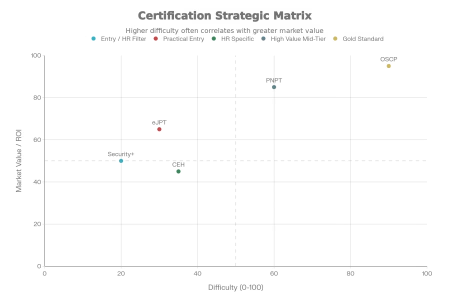
Certifications are the bridge between your self-study and the HR department. However, not all certs are created equal. We analyzed the Return on Investment (ROI) for the major certifications relevant in 2026.
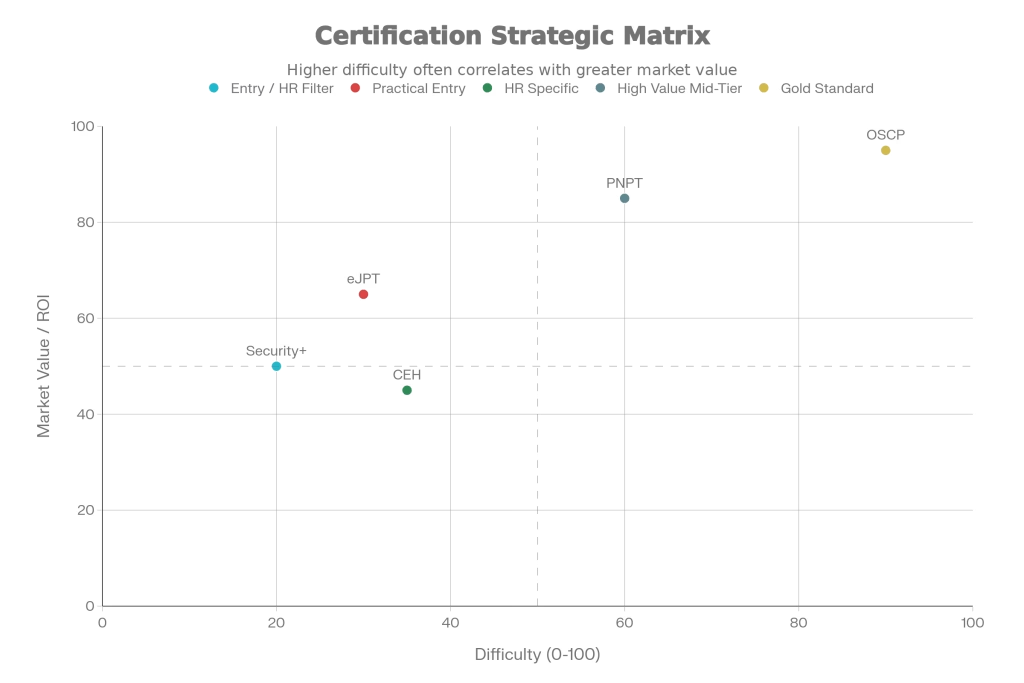
The “HR Filter” vs. The “Skill Prover”
| Certification | Level | Cost | Practicality | Verdict |
|---|---|---|---|---|
| CompTIA Security+ | Entry | Low | Low (Theory) | Mandatory First Step. It gets you past the automated HR filters for junior roles. |
| CEH (Certified Ethical Hacker) | Entry/Mid | High | Low (Multiple Choice) | Controversial. Expensive and viewed as outdated by technical leads, but still loved by HR and government contracts. Get it only if a job requires it. |
| eJPT (eLearnSecurity) | Entry | Low | High (Hands-on) | Best Starter. A fantastic, affordable practical exam for legitimate beginners. |
| OSCP (Offensive Security) | Advanced | High | Very High | The Gold Standard. “Try Harder.” It is difficult, stressful, and widely respected. Having this proves you can handle the pressure. |
| PNPT (TCM Security) | Mid | Mid | Very High | The Modern Rival. Focuses on real-world scenarios (OSINT, AD, Reporting) rather than just “Capture the Flag.” Gaining rapid industry respect. |
Expert Note: If you are on a budget, the PNPT offers incredible value and teaches modern Active Directory attacks better than many legacy courses. However, the OSCP remains the “King” for resume recognition globally, from the UK to Cyprus to the US.
The “Bridge”: From Theory to Practice
This is the hardest part of the journey. You have read the books, you have watched the videos, but you have no experience. How do you bridge the gap?
Build a Home Lab
Don’t rely solely on cloud labs. Build a virtual environment on your own hardware.
- Hypervisor: VirtualBox or VMware.
- Victims: Metasploitable, Windows 10 Evaluation ISOs, Windows Server 2019.
- Attacker: Kali Linux or Parrot OS.
- Goal: Set up a Domain Controller, join a Windows 10 PC to the domain, and try to hack it. This teaches you sysadmin skills, which makes you a better hacker.
Capture The Flag (CTF) Platforms
Gamified learning is effective, but treat it as practice, not the real world.
- Hack The Box (HTB): Excellent for keeping skills sharp. The “Pro Labs” simulate corporate networks.
- TryHackMe: The best starting point for guided learning paths.
Bug Bounties
This is your “Internship.” Platforms like HackerOne or Bugcrowd allow you to legally hack real companies.
- Strategy: Don’t aim for Google or Facebook immediately. Look for smaller programs.
- Value: Finding even one valid bug allows you to put “Freelance Security Researcher” on your resume with proof.
The Art of Reporting
Here is a hard truth: You are not paid to hack; you are paid to write a report.
If you hack the bank but cannot explain how to fix it to the CEO, you have failed.
- Practice writing reports for your CTF challenges.
- Include an “Executive Summary” (non-technical) and “Technical Findings” (technical).
- Use a professional tone. No “I pwned the server.” Instead: “We identified a remote code execution vulnerability.”
Emerging Tech for Your How to Become a Penetration Tester Journey
To future-proof your career, you must look beyond traditional network pentesting. The 2026 landscape is shifting toward three pillars.
Cloud Penetration Testing
With infrastructure moving to AWS, Azure, and Google Cloud, the perimeter has dissolved.
- Focus: IAM misconfigurations, S3 bucket leaks, Serverless function exploitation.
- Action: Learn the basics of at least one major cloud provider.
AI and LLM Security
As companies integrate Large Language Models (LLMs), securing them is the new frontier.
- Focus: Prompt injection, data leakage, model poisoning.
- Action: Understand how APIs interact with AI models.
API Security
The world runs on APIs. Mobile apps, web apps, and IoT devices all communicate via APIs.
- Focus: Broken Object Level Authorization (BOLA), Excessive Data Exposure.
- Action: Master Postman and Burp Suite’s API testing capabilities.
Step-by-Step: How to Become a Penetration Tester in 2026
We analyzed thousands of job postings and forum discussions to identify the specific skills that separate successful applicants from the resume pile. Here is the CyberPhiLearn recommended path:
Phase 1: The Foundation (Months 1-3)
- Study: Network+ and Security+ content (Certification optional, knowledge mandatory).
- Practice: Install Linux as your daily driver or in a VM. Learn the command line.
Phase 2: The Practical Basics (Months 4-6)
- Cert: eJPT (eLearnSecurity Junior Penetration Tester).
- Lab: Complete the “Junior Penetration Tester” path on TryHackMe.
- Coding: Write a simple port scanner in Python.
Phase 3: The Professional Shift (Months 7-12)
- Cert: PNPT or OSCP (Start studying).
- Experience: Participate in Bug Bounties or VDPs (Vulnerability Disclosure Programs).
- Networking: Join local OWASP chapters or discord communities. For professionals in tech hubs like Cyprus, local meetups are invaluable for networking.
Phase 4: The Job Hunt
- Portfolio: Create a GitHub repository with your scripts and sanitized pentest reports from your labs.
- Resume: Highlight methodologies and business impact, not just tools.
Conclusion
Becoming a penetration tester is a marathon, not a sprint. It requires a unique blend of technical acumen, creative problem solving, and the persistence to bang your head against a wall until you find a crack.
Ultimately, your success in learning how to become a penetration tester: 2026 career guide relies on your ability to adapt. The landscape rewards those who move beyond being “script kiddies” and embrace the role of a security consultant. It is about protecting data, understanding business risk, and communicating complex ideas simply.
Your Next Steps:
- Stop passively watching tutorials.
- Set up your home lab today.
- Pick one networking concept to master this week.
The path is open. The data shows the need is real. The rest is up to you.
Stay secure.
FAQ
Is it too late to get into cybersecurity in 2026?
No. While the entry-level market is competitive, the demand for skilled practitioners is higher than ever. The “shortage” is at the mid-senior level; if you can prove you have those skills early, you will be hired.
Do I need a college degree?
Analysis suggests that while degrees are helpful for HR filters, they are rarely the deciding factor for technical hiring managers. Experience, certifications, and a portfolio carry more weight.
Can I work remotely?
Yes, but many entry-level roles (especially in SOCs or junior consultancy) may require hybrid work for mentorship. Once established, penetration testing is highly conducive to remote work.
I have certifications but zero professional experience. How can I possibly get hired?
This is the #1 barrier for every junior, but it is solvable. In cybersecurity, “experience” does not strictly mean “paid employment.” You can manufacture your own valid experience immediately by doing three things:
1) Create “Public Proof”: Do not just finish a Hack The Box machine; write a detailed walkthrough and publish it on Medium or LinkedIn. This proves your methodology to a hiring manager better than a resume.
2) Hunt for Real Bugs: Sign up for a Bug Bounty program (like HackerOne). finding even one low-severity bug allows you to legally put “Freelance Security Researcher” on your CV.
3) Build Tools: Write a simple Python script that automates a task (e.g., a subdomain enumerator) and host it on GitHub. It shows you can build, not just break.The Bottom Line: Employers hire juniors who show passion through action. If you can show them what you’ve done, they won’t care as much about where you haven’t worked.