
Table of Contents
Introduction
The Github repository I maintain for small business security tools receives a recurring question that reveals a critical knowledge gap: “Is penetration testing just for enterprises?” This misconception costs small businesses dearly. In Q1 2025 alone, 73% of SMBs faced ransomware attacks, yet fewer than 15% had conducted any form of penetration testing. Penetration testing for small businesses is a systematic security assessment where ethical hackers simulate real-world cyberattacks to identify vulnerabilities before criminals exploit them—and it’s no longer optional in today’s threat landscape.
The Mediterranean cybersecurity market, where I’ve observed both Cyprus and broader European trends, shows a troubling pattern: small businesses treat security as an afterthought until breach costs force reactive spending. My work developing IoT security frameworks exposed me to countless small manufacturers who assumed their size made them invisible to attackers. They learned otherwise when supply chain compromises cascaded through their networks.
This article demystifies penetration testing specifically for small business contexts. I’ll address the confusion between security audits and pen tests, break down realistic budget options, explain why 2025’s threat landscape demands proactive testing, and show you how to measure actual ROI from security investments. Whether you’re navigating cyber insurance requirements or simply trying to protect customer data, you’ll understand exactly what penetration testing means for businesses operating without enterprise security budgets.
Let me share what five years of security specialization and academic research have taught me about making pen testing accessible and effective for small business owners.
What is Pen Testing for Small Business
Penetration testing simulates cyberattacks against your business systems to find security weaknesses before criminals do. Unlike automated vulnerability scans that simply identify known issues, pen testing involves skilled security professionals actively attempting to breach your defenses using the same techniques as real attackers. For small businesses, this means getting a realistic picture of how your website, network, customer database, or cloud infrastructure would hold up against actual threats.
Think of it this way: vulnerability scanning is like checking if your doors and windows have locks. Penetration testing is hiring someone to actually try breaking in using lockpicks, finding the window you forgot about, or discovering that your “locked” back door can be opened with a credit card. The difference matters enormously.

The Core Components
Reconnaissance and information gathering. Testers research your business exactly as attackers would—examining your website, social media, employee LinkedIn profiles, and publicly available technical details. My Github security tools demonstrate how much information leaks from seemingly innocent sources. One small Cyprus-based retailer I consulted for had inadvertently exposed their entire network architecture through job postings seeking IT help.
Vulnerability identification and exploitation. This is where ethical hackers move beyond detection to active testing. They don’t just note that your login page might be vulnerable to brute force attacks—they actually attempt the attack in a controlled manner. They try SQL injection against your database, test whether your Wi-Fi network can be compromised, and probe your email systems for phishing susceptibility.
Privilege escalation and lateral movement. After gaining initial access, testers determine how far they can penetrate. Could a compromised employee account access financial systems? Can they move from your public website to internal databases? This mirrors exactly how ransomware operators work—they rarely succeed with a single exploit, but rather chain multiple vulnerabilities together.
Documentation and remediation guidance. You receive detailed reports showing not just what’s vulnerable, but how it was exploited, what data was accessed, and specific steps to fix each issue. Quality pen testing provides actionable remediation, not just scary findings.
Typical Testing Scope
Your external attack surface—the systems visible to the internet like websites, email servers, and remote access portals. This is where 68% of small business breaches originate according to 2025 data. A local accounting firm I worked with discovered their client portal, built five years ago and never updated, had seventeen critical vulnerabilities that would have taken attackers less than an hour to exploit.
Internal network testing examines what happens if an attacker gains a foothold—through phishing, physical access, or a compromised laptop. With 45% more remote work vulnerabilities in 2025 compared to 2019, this has become critical. Your employee working from the coffee shop represents a potential entry point that pen testing should evaluate.
Application testing focuses on custom software, web applications, or mobile apps your business uses. Even if you didn’t develop them internally, third-party applications integrated with your systems create risk. The IoT devices I studied during my PhD research at University of York showed how connected systems multiply attack vectors—a vulnerability in your smart thermostat could theoretically provide network access.
What Penetration Testing is NOT
It’s not a one-time compliance checkbox. I’ve seen too many small businesses treat pen testing like a fire inspection—something you do once to satisfy insurance requirements, then forget about. Your threat landscape evolves constantly. That “secure” system tested in January 2025 may have new vulnerabilities by June.
It’s not a replacement for basic security hygiene. Pen testing won’t fix poor password policies, missing software updates, or lack of employee training. One small business owner told me, “We got pen tested, so we’re secure now,” while their team still shared a single admin password written on a sticky note. Pen testing identifies problems; you must implement solutions.
It’s not necessarily expensive or disruptive. This misconception prevents many small businesses from even considering it. Budget-friendly options exist (which I’ll detail in the next section), and professional testers work to minimize operational disruption. The Cyprus manufacturing company I mentioned earlier completed their pen test during normal business hours without any customer-facing downtime.
The small business context matters significantly. Enterprise pen testing might involve months of testing, dozens of systems, and six-figure budgets. Your small business version should be proportionate—focused on your actual critical assets, scaled to realistic threats you face, and priced for small business budgets.
Pen Testing Cost: Small Business Budget-Friendly Alternatives
The “penetration testing is too expensive” objection dominates every small business security conversation I have. Let me address this directly with actual numbers and realistic alternatives.
Understanding the Real Cost Landscape
Traditional full-scope penetration testing from established security firms typically ranges from $5,000 to $25,000 for small businesses. These engagements usually involve 40-80 hours of testing, detailed reporting, and remediation support.
However, the penetration testing market has evolved dramatically. You now have options that didn’t exist even three years ago.
Budget-Friendly Alternatives That Actually Work
Focused scope penetration testing addresses your highest-risk assets only. Instead of testing everything, you identify your crown jewels—perhaps your e-commerce checkout system, customer database, or remote access portal. A focused test on 2-3 critical systems typically costs $1,500-$4,000.
A Cyprus-based online retailer I consulted for had limited budget but processed credit card transactions. We scoped their pen test exclusively to their payment processing flow and customer data storage. The $2,200 investment identified a critical vulnerability that could have resulted in a PCI compliance violation worth potentially $50,000 in fines.
Automated penetration testing platforms leverage AI and standardized testing methodologies to reduce costs. Services like Cobalt, Synack, or HackerOne offer “pen testing as a service” starting around $500-$2,000 monthly. These platforms combine automated scanning with human verification, providing continuous testing rather than annual snapshots.
Bug bounty programs for small businesses allow you to set bounties for security researchers who find vulnerabilities in your systems. You only pay when vulnerabilities are discovered and verified. Some small businesses start with bounties as low as $100-$500 per finding.
Hybrid approaches combining tools and expertise offer middle-ground solutions. You can run automated vulnerability scans yourself using tools like OWASP ZAP (free), Nessus Essentials (free for limited use), or Burp Suite Community Edition (free), then hire a security consultant for 8-10 hours ($800-$2,000) to validate findings and attempt actual exploitation.
Small Business Security Audit vs Penetration Testing: Key Differences
The confusion between security audits and penetration testing creates real problems for small business owners trying to make informed security decisions. I’ve consulted for businesses that paid for “security audits” expecting penetration testing, and vice versa. Understanding these distinctions prevents wasted money and ensures you’re actually getting the security validation you need.

Security Audits: Comprehensive Compliance and Policy Review
A security audit systematically examines your security policies, procedures, and controls against established standards or frameworks. Think of it as a detailed inspection of your security program’s documentation, implementation, and governance.
Security audits typically assess:
Policy and procedure documentation. Do you have written security policies? Are they current, comprehensive, and actually followed? Auditors review your acceptable use policies, incident response plans, data classification schemes, and access control procedures.
Compliance with regulatory requirements. For businesses subject to GDPR, PCI-DSS, HIPAA, or industry-specific regulations, audits verify compliance. This includes reviewing how you handle customer data, whether you maintain required logs, if you conduct mandatory training, and whether your data retention practices meet legal requirements.
Control effectiveness and implementation. Auditors examine whether your security controls actually work as designed. Do employees really use the password complexity requirements in your policy? Are software updates applied according to your patch management procedure?
Configuration reviews and baseline comparisons. Security audits often include reviewing system configurations against security baselines—industry standards like CIS Benchmarks or vendor recommendations.
Penetration Testing: Adversarial Security Validation
Penetration testing takes an attacker’s perspective, actively attempting to compromise your systems regardless of what your policies say should happen. It’s practical, hands-on security validation.
Penetration testing focuses on:
Active exploitation of vulnerabilities. Testers don’t just identify that your login page might be vulnerable to brute force attacks—they actually attempt the attack. They try to bypass your firewall, inject malicious code into your database, or compromise employee accounts through social engineering.
Real-world attack simulation. Pen testers use the same tools, techniques, and procedures as actual cybercriminals. They chain multiple vulnerabilities together, escalate privileges, and demonstrate the full impact of successful attacks.
Technical vulnerability validation. While audits might note that your web application should implement input validation, penetration testing actually tests whether that validation can be bypassed.
Impact demonstration. Pen test reports show exactly what data could be stolen, which systems could be disrupted, and how much damage an attacker could cause.
Key Differences That Matter
Approach: Audits examine your security program through documentation review, interviews, and observation. Penetration testing actively tries to break in.
Objective: Audits primarily verify compliance with standards, regulations, or policies. Penetration testing validates whether your defenses actually work against real threats.
Scope: Security audits typically review your entire security program—policies, procedures, training, physical security, vendor management. Penetration testing focuses specifically on technical vulnerabilities in your systems, networks, and applications.
Output: Audit reports recommend improvements based on best practices. Pen test reports provide proof of exploitable vulnerabilities with evidence of actual compromise.
When You Need Each
You need a security audit when:
- Pursuing compliance certifications (ISO 27001, SOC 2, PCI-DSS)
- Required by contracts, insurance, or regulations
- Establishing a new security program and need baseline assessment
- Responding to audit findings from regulators or business partners
You need penetration testing when:
- Validating whether your systems can withstand actual attacks
- Required by cyber insurance for coverage or renewal
- Launching new applications, websites, or infrastructure
- After significant security incidents to verify remediation
- Preparing for high-risk periods (holiday shopping, tax season)
You need both when:
- Comprehensive security assurance is required
- Regulatory frameworks demand both compliance and security testing
- Cyber insurance requires demonstrated due diligence
- Protecting high-value assets or sensitive customer data
Why Small Businesses Need Penetration Testing in 2025
The threat landscape targeting small businesses has fundamentally changed, and the “we’re too small to be targeted” assumption is not just wrong—it’s dangerous.
The 2025 Threat Reality
You’re actively targeted, not collateral damage. The 73% of SMBs facing ransomware attacks in Q1 2025 weren’t random victims—they were deliberately chosen. Cybercriminals specifically target small businesses because they typically have weaker defenses than enterprises but more valuable data than individual consumers.
Supply chain attacks cascade through small vendors. The 68% year-over-year increase in supply chain attacks disproportionately affects small businesses. You might serve larger enterprises as vendors, suppliers, or service providers. Attackers compromise your weaker security to reach your better-protected customers.
Cyber insurance now mandates security validation. The insurance landscape shifted dramatically in 2024-2025. Most cyber insurance policies now require annual penetration testing for coverage above $1M or for renewal of existing policies.
Regulatory enforcement targets small businesses. The €1.2B in GDPR fines levied against SMBs in 2024 represents an enforcement shift. Regulators increasingly hold small businesses to the same data protection standards as enterprises.
Remote work expanded your attack surface. The 45% increase in vulnerabilities associated with remote work since 2019 hasn’t stabilized—it’s still growing. Your small business now has employees accessing systems from home networks, coffee shops, and travel locations.
Specific 2025 Threats Requiring Testing
AI-powered phishing has become sophisticated enough to fool even security-aware employees. Attackers use AI to craft personalized phishing emails that reference real projects, colleagues, and business contexts.
Ransomware-as-a-service means even unsophisticated attackers can deploy enterprise-grade ransomware. The barrier to launching attacks has dropped to near zero.
IoT and connected device vulnerabilities multiply risk, especially for small businesses adopting smart building systems, connected security cameras, or industrial IoT devices.
Cloud misconfiguration exploitation affects small businesses rapidly adopting cloud services without adequate security expertise. Amazon S3 buckets left publicly accessible, Azure storage with weak authentication—these misconfigurations are invisible until pen testing exposes them.
Business Continuity and Competitive Advantage
Customer trust and contract requirements. Your customers increasingly require security validation before doing business. RFPs now commonly include questions about penetration testing frequency and findings.
Incident response preparation. Penetration testing reveals not just vulnerabilities but also how well you detect and respond to attacks. Do your monitoring systems alert when pen testers compromise accounts?
Investment protection. Small businesses are investing in digital transformation—e-commerce, cloud migration, mobile apps. Penetration testing ensures these investments are secure.
Pen Testing ROI: Measuring Small Business Security Improvements
“How do I justify the cost to my business partner?” This question appears in nearly every penetration testing consultation I conduct. Let me show you how to quantify penetration testing ROI using practical frameworks.
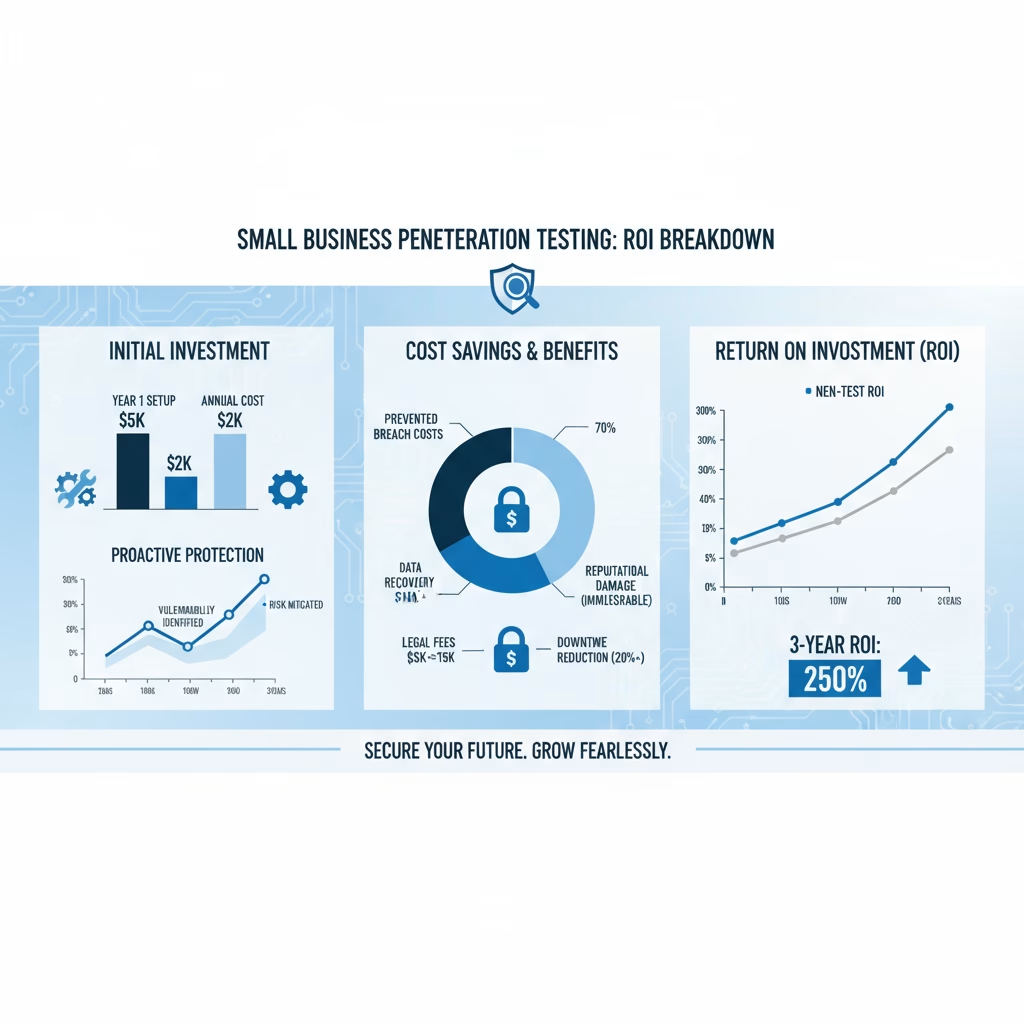
Direct Financial ROI Calculations
Breach cost avoidance represents the most straightforward ROI measurement. The 2025 IBM Cost of Data Breach Report shows small business breaches averaging $148,000 in total costs.
Calculate your potential breach cost:
- Customer records at risk × $180 per record (2025 average)
- Plus regulatory fines (€20,000-€50,000 for GDPR violations)
- Plus business downtime cost (daily revenue × estimated days offline)
- Plus reputation damage (typically 20-30% of annual revenue)
A small e-commerce business with 10,000 customer records faces potential breach costs of approximately $2M total exposure. Their $4,000 annual penetration testing investment represents 0.2% of potential breach costs.
Insurance premium optimization provides measurable annual savings. Cyber insurance carriers offer premium discounts of 20-40% for documented penetration testing. A small business paying €3,000 annually for cyber insurance might reduce premiums to €2,000 with pen testing evidence—a €1,000 annual saving.
Compliance fine avoidance delivers quantifiable ROI. GDPR fines for small businesses typically range from €20,000-€50,000 for first violations involving inadequate security. PCI-DSS violations can cost $5,000-$100,000 monthly until remediated.
Indirect Value Metrics
Customer retention and acquisition. Security breaches cause customer loss averaging 25-30% for small businesses. Demonstrating proactive security testing helps retain existing customers and win new business.
Competitive advantage in RFPs. Small businesses competing for contracts increasingly face security questionnaires. Documented penetration testing provides competitive differentiation.
Reduced incident response costs. Businesses that conduct regular penetration testing respond to actual incidents 3-4 times faster than those without testing experience.
Team security awareness improvements. The security findings and remediation process educate your team about real threats, improving overall security culture.
ROI Calculation Framework
Simple ROI formula:
ROI = (Avoided Costs - Testing Investment) / Testing Investment × 100%
Example calculation:
- Annual pen testing cost: $3,000
- Avoided breach cost (conservative estimate): $150,000
- Insurance premium savings: $1,000
- Compliance fine avoidance: $25,000
ROI = ($176,000 - $3,000) / $3,000 × 100% = 5,766% ROIEven with extremely conservative estimates (preventing just one minor incident), penetration testing delivers measurable positive ROI.
Frequently Asked Questions
How often should small businesses conduct penetration testing?
Annual penetration testing provides baseline security validation for most small businesses. However, you should also test after significant changes: launching new applications, major infrastructure updates, cloud migrations, or after security incidents. High-risk businesses (handling payment cards, healthcare data, financial services) should consider quarterly testing of critical systems.
Will penetration testing disrupt my business operations?
Professional penetration testers work to minimize disruption. External testing (websites, email, remote access) typically causes no noticeable impact. Internal testing may require brief system access but is usually scheduled during low-activity periods. Discuss timing and scope with your testing provider to ensure business continuity.
Can I do penetration testing myself using free tools?
Free tools like OWASP ZAP, Nessus Essentials, and Metasploit provide valuable capabilities for vulnerability scanning. However, penetration testing requires expertise in exploitation techniques, attack chaining, and realistic threat simulation. Consider using free tools for continuous monitoring between professional penetration tests rather than as a replacement.
What should I look for when choosing a penetration testing provider?
Look for certifications (OSCP, CEH, GPEN), relevant industry experience, clear methodology and scope definition, detailed reporting with remediation guidance, professional liability insurance, and transparent pricing. Ask for references from similar-sized businesses in your industry. Avoid providers who can’t clearly explain their testing approach or guarantee unrealistic results.
Do I need penetration testing if I’m already using antivirus and firewalls?
Yes. Antivirus and firewalls are essential preventive controls, but they don’t validate your overall security posture. Penetration testing examines whether your combination of security controls effectively protects against real-world attacks. Many breaches occur despite antivirus and firewalls due to misconfigurations, unpatched systems, or weaknesses those tools don’t address.
Conclusion
Penetration testing for small businesses isn’t optional anymore—it’s essential infrastructure in 2025’s threat landscape. The misconception that penetration testing is only for large enterprises with unlimited budgets has been thoroughly debunked by both market evolution and threat reality.
With focused testing starting at $1,500, automated platforms from $500 monthly, and hybrid approaches combining free tools with expert validation, budget constraints no longer justify skipping security validation. When cyber insurance discounts offset 30-50% of testing costs and average breach costs exceed $148,000, the ROI calculation is straightforward.
The small businesses succeeding in 2025 are those treating penetration testing as essential business infrastructure—not optional security theater. They understand that their size makes them targets, not invisible. They recognize that customer trust, regulatory compliance, and competitive advantage all depend on demonstrated security.
Your first penetration test reveals uncomfortable truths about your security posture. But those uncomfortable truths discovered by ethical hackers you hired are far better than the catastrophic discoveries made by criminals targeting your business.
Start with focused testing on your highest-risk systems. Use the budget-friendly alternatives I’ve outlined. Measure ROI using the frameworks provided. But start. The threat landscape isn’t waiting for you to feel ready, and neither should your security validation.
References
- https://deepstrike.io/blog/penetration-testing-startups-small-business
- https://www.softwaresecured.com/post/penetration-testing-roi-5-metrics-to-communicate-real-value
- https://laburity.com/cybersecurity-roi-explained-why-investing-in-penetration-testing-saves-your-business/
- https://redbotsecurity.com/executive-guide-that-demystifies-penetration-testings-value-proposition/
- https://penstrike.io/blog/the-roi-of-penetration-testing-investing-in-security-to-save-your-business-money/
- https://morethandigital.info/en/roi-of-penetration-testing-a-strategic-investment-in-cybersecurity/
- https://zelvin.com/roi-of-penetration-testing/
- https://cybercx.com.au/resource/penetration-testing-guide/
- https://cloudguard.ai/wp-content/guides/cloudguard-cyber-roi-business-case-guide.pdf
- https://creaplus.com/blog-en/cybersecurity-that-pays-off-the-real-roi-for-small-and-medium-businesses/
