A harmful cyber-attack known as Superna Ransomware is an increasing trend in all organizations. The way that this attack works is that it encrypts the data and files of your computer and demands payment to decrypt it. In other words, a ransomware attack converts your files stored in the computer to an unreadable format. For example, you cannot open your text or word document because your computer cannot read and open it properly. To revert the files to their original format, called decryption process, it requires the help of the hacker. For this reason, hackers demand a large amount of money from owner to stop the attack and decrypt the corrupted files. Apart from that, attacker use cryptocurrencies as a payment method to keep them untraceable.
Superna Ransomware Spread Steps
Many cyber attacks, as described in our post Top 10 Cyber Threats (Part I) and Part II here, infect users mostly by email. The image depicts that usually a phishing email with an embedded malicious link is usually the entry point. Once the victim clicks the link, it lands to a malicious website that contains a malware. The last step is that malware is automatically or manually downloaded to the victim’s computer and the encryption process begins.
Once the files are encrypted, the only way to revert them is to find the decryption key. For this reason, many victims, people and organization, succumb to hackers and pay the demand to get the key. However, there are times that hackers do not
Encryption vs Decryption Process
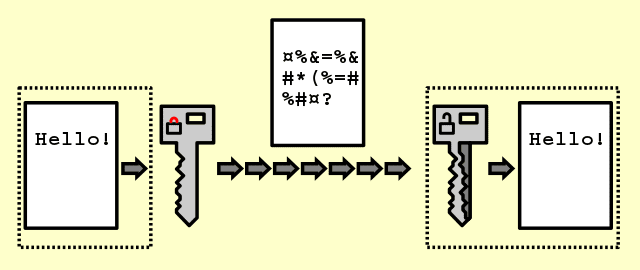
It is useful for an average user to know and understand what is encryption and decryption. In the world of computers, those terms are found in Cryptography lessons. Generally, a piece of information has two states; it can be read by someone and it is called plaintext, or it can be secret or encrypted, called ciphertext. The process of converting the information into random characters is known as Encryption.
Encrypting data requires a cryptographic key. This key is usually a string of characters that are used in the encryption algorithm to alter data and convert them into a format that seems to be random. Like in physical world, you lock (encrypt) your valuable items in a lockbox (computer) that you can only open with the right PIN (cryptographic key). In the cyber world, encrypting (locking) your data requires a key (string of characters) to convert them into random characters. Encryption converts the plaintext into ciphertext. The longer the cryptographic key, the more difficult it can be to find it.
Decrypting your data is the reverse process of encryption. Actually, if you have the correct cryptographic key, the random information will be converted back to useful piece of data. This is how most well-known cryptographic algorithms work.
The picture below shows an example of how encrypted files appear on a computer with Ransomware. As it can be seen, files do not have a known file extension but appear in a strange format. That means the malware encrypted them and now demands money from the user.
Encryption Algorithms
There are many encryption algorithms avaialble. Thera are two categories of algorithms, symmetric and asymmetric.
Symmetric algorithms use the same key for both encryption and decryption. On the other hand, asymmetric algorithms use different encryption key and decryption key. Some well-known symmetric encryption algorithms are:
- AES (Advanced Encryption Standard)
- DES (Data Encryption Standard)
- 3-DES
Some well-known asymmetric encryption algorithms are:
- RSA (Rivest–Shamir–Adleman)
- Elliptic curve cryptography
Protection Methods
How can you protect yourself from Superna Ransomware attacks? Let’s see some simple ways:
- Install Antivirus and Antimalware software (Free or Paid software can protect you) and Scan regularly your computer to keep it healthy.
- Don’t share with anyone your secrets or passwords for any reason.
- Avoid clicking links included in malicious emails. Be suspicious with any email that don’t seem to be legitimate.
- Avoid visiting malicious websites that include free pirated software or adult content.
- Check the “Sender” field on each email to ensure that is not a hacker’s email.
- Don’t install suspicious applications to your mobile (make sure to see app reviews).
- Take frequent backups to an external drive on in cloud. In this way, you keep your files safe in case you get infected.
Conclusion
Superna Ransomware attacks are increasing day by day. Hackers find it a good solution to lock your personal files and demand money to get them back. For this reason, users should regularly take backup files so that if you lose them or you get a superna ransomware, you will already have your files. Unfortunately, big organizations don’t have security measures to avoid this type of attacks. Taking some simple steps as described previously, could help avoid situations where hackers could steal a large amount of money.



